Networking
CIDR (Classless Inter Domain Routing)
method for allocating IP address
- CIDR not should overlap for peering
- the max CIDR size in AWS is /16.
Parts of CIDR
- Base IP address eg 10.0.0.1
- Subnet mask: how many bits can change in IP
- /0 = 0.0.0.0 = all octet can change
- /8 = 255.0.0.0 = last 3 octet can change
- /16 = 255.255.0.0 = last 2 octet can change
- /24 = 255:255.255.0 = last 1 octet can change
- /32 = 255.255.255.255 = no octet can change
Number of IPs formula
/28
=> 2^(32-28)
=> 2^4)
=> 16 IPs
Example
- 192.168.0.0/24 -> (192.168.0.0 .. 192.168.0.255) = 256 IP
- 192.168.0.0/16 -> (192.168.0.0 .. 192.168.255.255) = 65536 IP
- 192.168.0.0/32 -> (192.168.0.0) = 1 IP
- 0.0.0.0/32 -> allIP
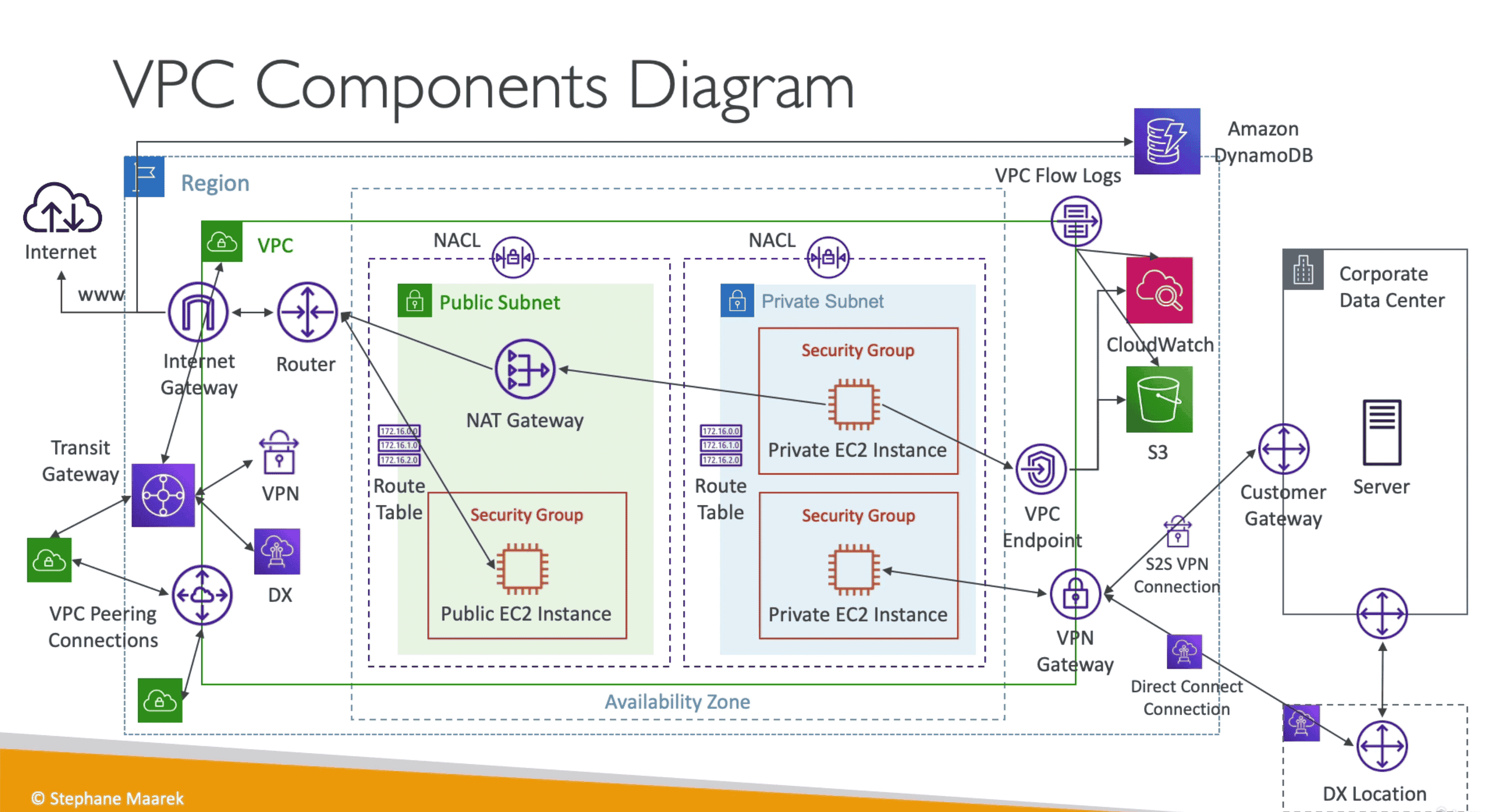
AWS VIRTUAL PRIVATE CLOUD (VPC)
Private Network in AWS help with isolation of resources
- Each Region have different VPC
- Max 5 VPC per region
- Max 5 CIDR per VPC
- CIDR size: Min
16IP(/28), Max65536(/16) - Allowed IPV4 range:
10.0.0.0/8<- Internet Private IP172.6.0.0/12<- AWS Default VPC IPV4192.168.0.0/16<- Home internet
- You can’t have a VPC with only a public subnet and AWS Site-to-Site VPN.
Default VPC
- All AWS Account get default VPC
- Connect with Internet & have public IPV4
- Have public & Private IPV4 DNS
- All new EC2 start withing default VPC if subnet is not defined
Subnets
Chunk of IP address in VPC for grouping of resources.
- AWS
Reserve first 4 & 1 Last IPin CIDR : eg 10.0.0.0/24- Network Address :10.0.0.0
- VPC Router: 10.0.0.1
- Mapped to AWS provided DNS: 10.0.0.2
- Future Use: 10.0.0.3
- Network Broadcast Address: 10.0.0.255
1. Public Subnet:
Connect with Internet with help of Internet Gateway(IGW)
- Should be smaller range than Private Subnet
- Example: 10.0.0.0/24 = 256 IP address
2. Private Subnet:
No Internet for private resources provide a VPN
- Should be large number of IP address for Private resources
- Example: 10.0.16.0/20 = 4091 IP address
Internet Gateway(IGW)
Help resourced in VPC connect to Internet with help of Route table
- Scale Horizontally, highly available & redundant
- Created independent of VPC
- Can connect with 1 VPC only
- Must have a route table to connect to Internet
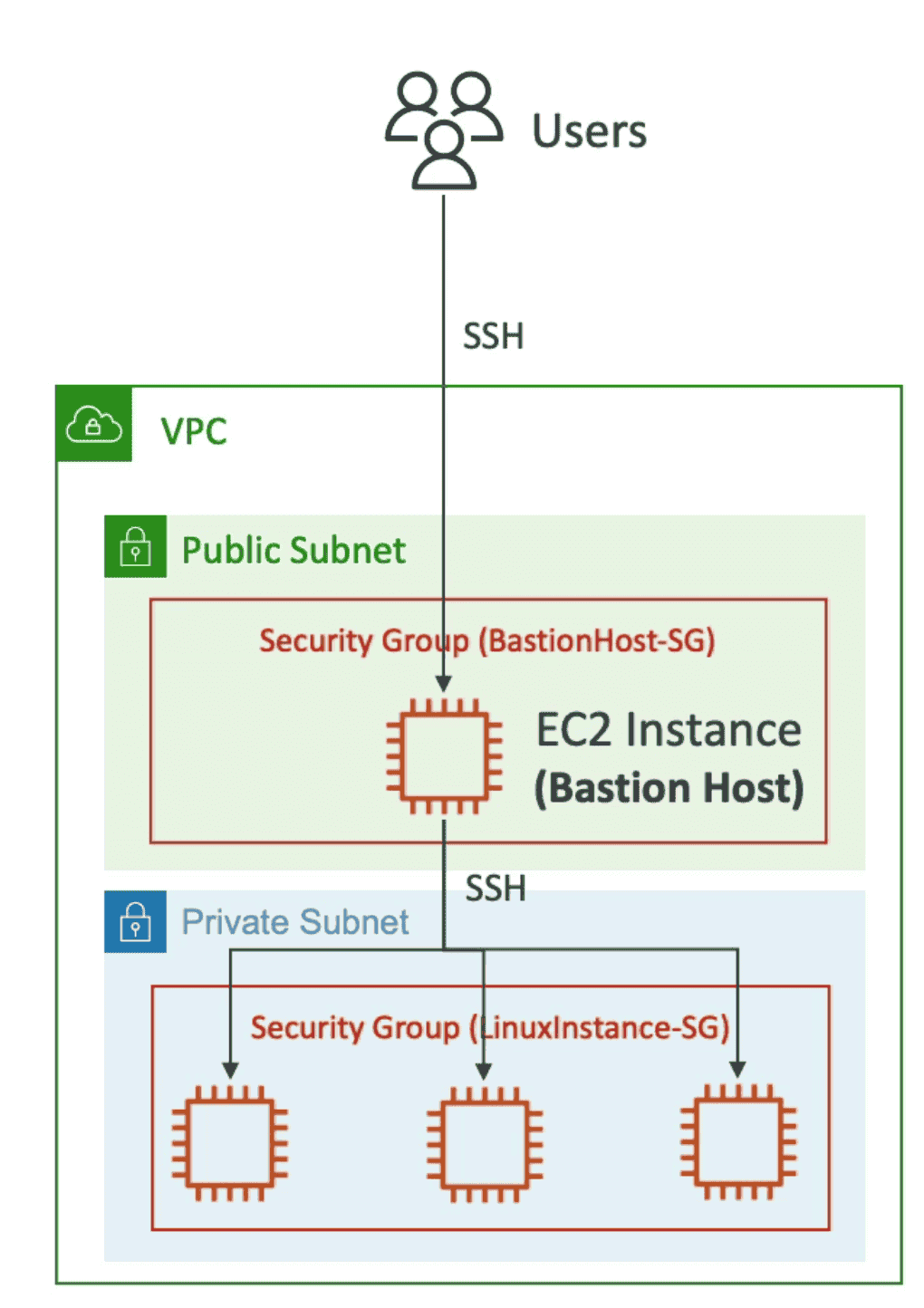
Bastian Host
- SSH into EC2 instance in Private subnet
- Host live in public Subnet
- SSH into host which in turn SSh into EC2 instances into Private Subnet
- EC2 Instance in Private Subnet should have security group to allow connection with HOST
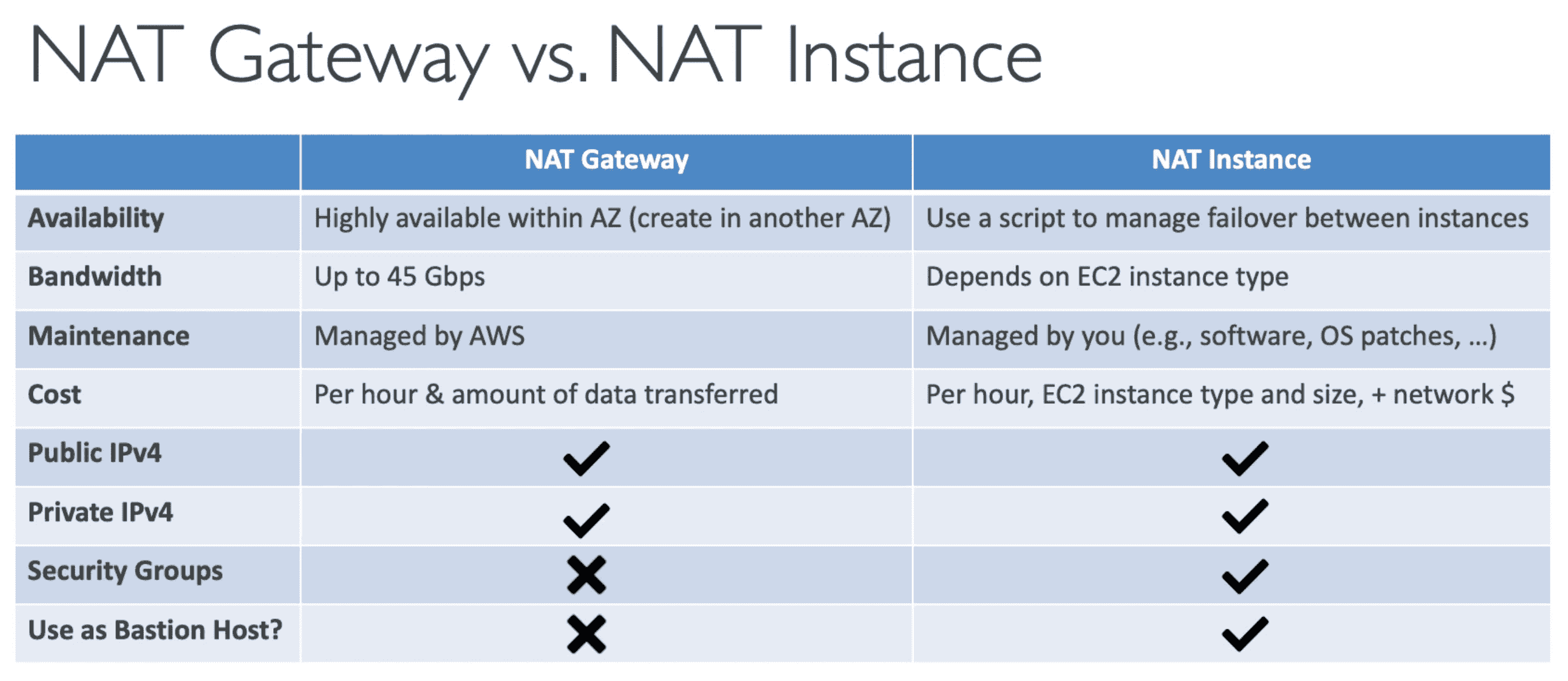
NAT Instance(Network Address Translation)
Allow EC2 Instance in Private subnet to connect to EC2 instance
- Deprecated in favour of NAT Gateway
- NAT instance launched in public subnet and connect with internet using public Elastic IP
- NAT translate packet from EC2 instance from private subnet to Internet & route back to EC2 in private subnet
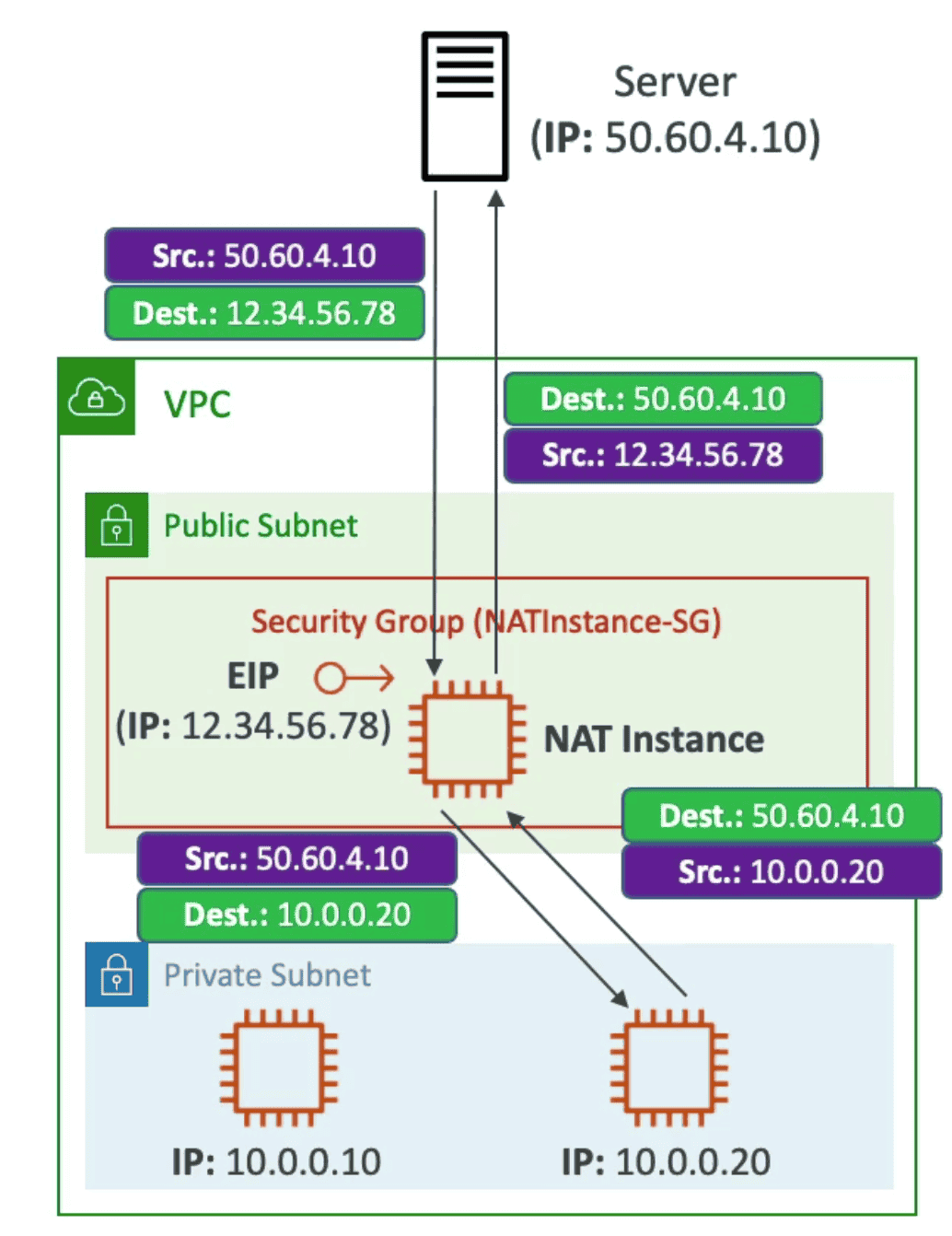
- NAT instance can be used as a bastion server
- Security Groups can be associated with a NAT instance
- NAT instance supports port forwarding
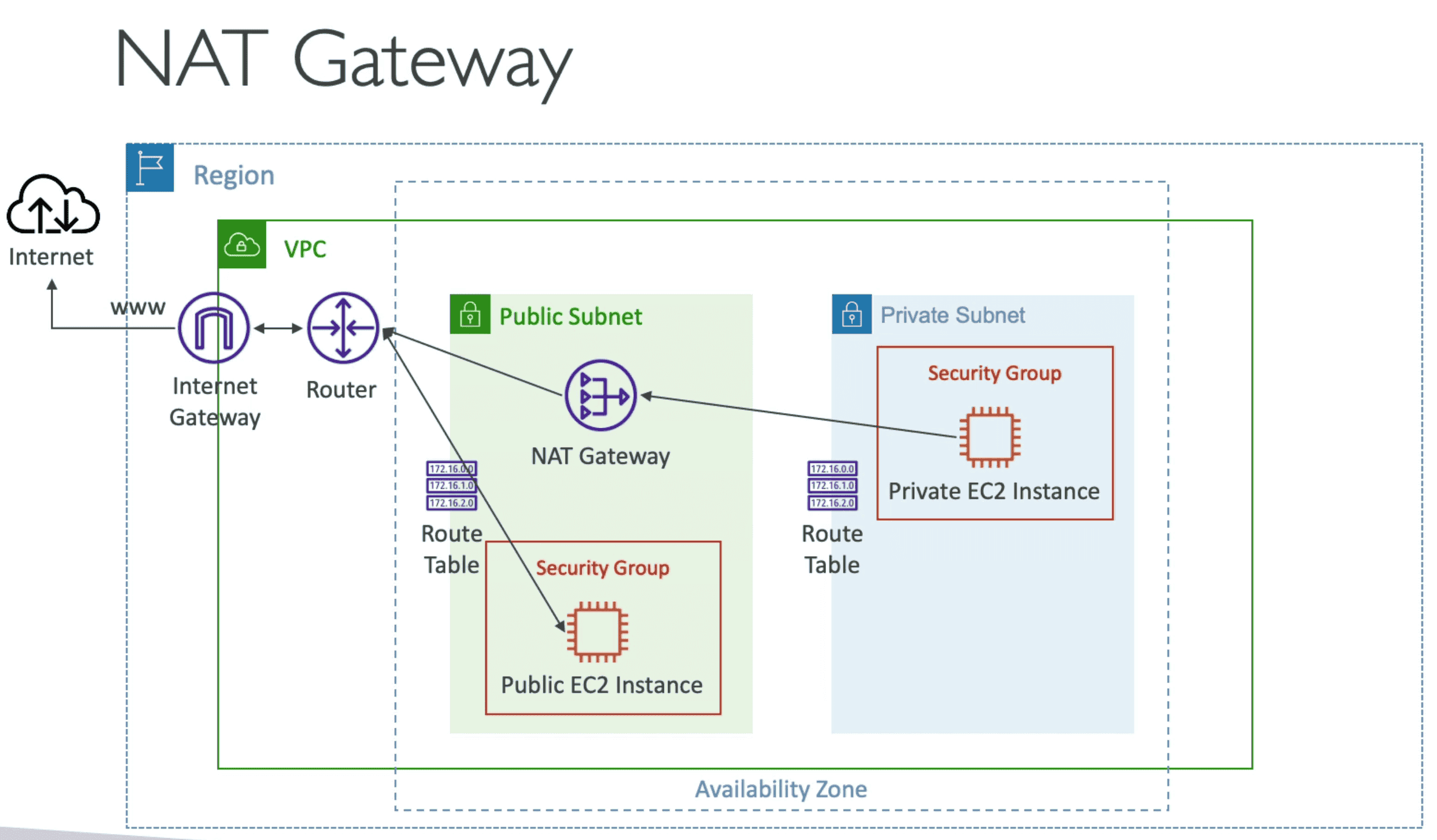
NAT Gateway/Virtual Private Gateway:
Created in Public VPC to help Connect with Internet
- AWS Manged NAT Instances
- Higher Bandwidth, High availability, No Admin required
- Pay per hour & bandwidth used
- Created in specific AVZ & use ELASTIC IP & work without security group
- Bandwidth
5GBps, Scale up to45 Gbps - Cant work without IGW
- Each AVZ have own NAT Gateway
- NAT instance CAN'T be used as a bastion server
- Security Groups CAN'T be associated with a NAT instance
- NAT instance DOES'T supports port forwarding
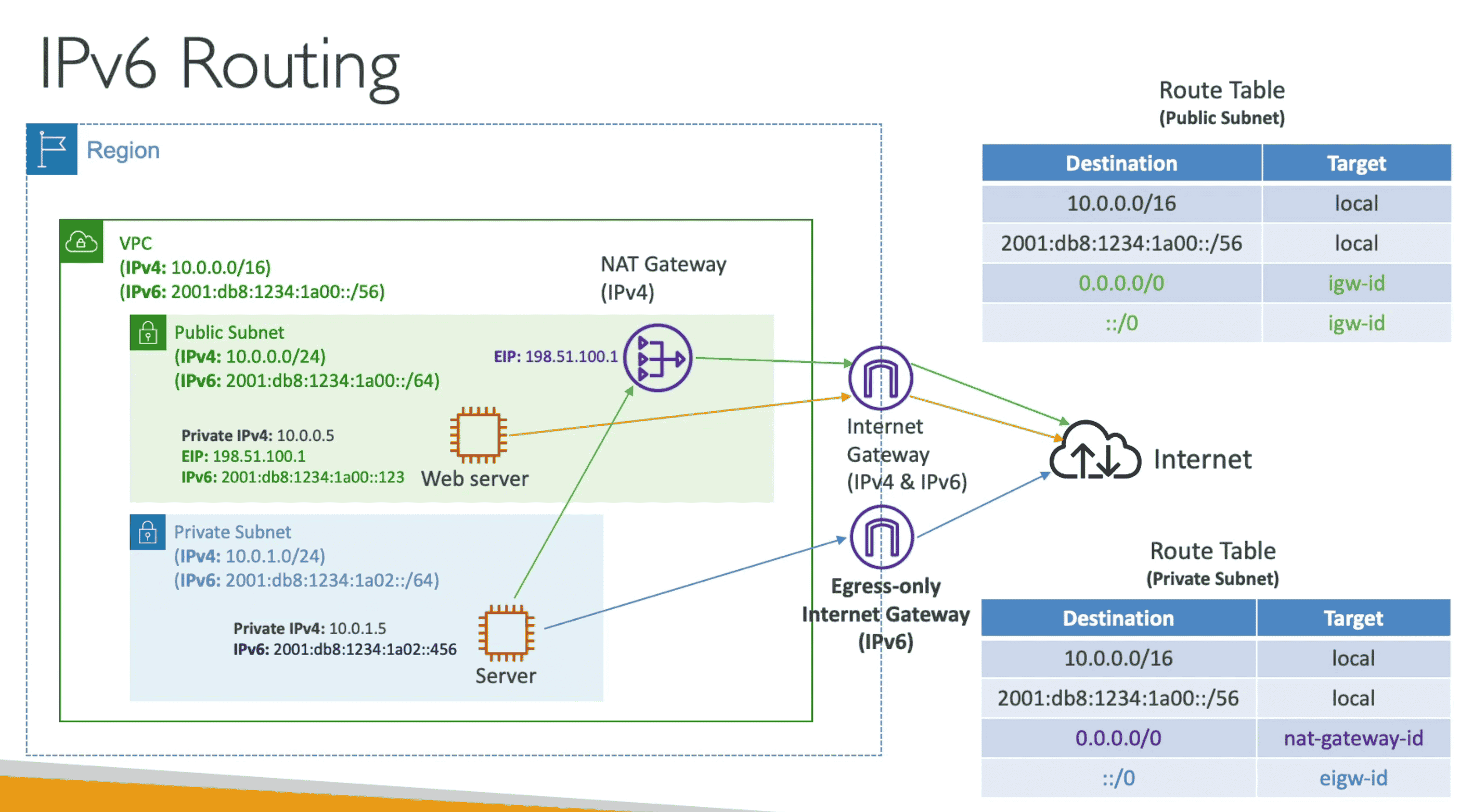
Egress Only Internet Gateway
NAT Gateway for IPV6
- Allow connecting with Internet with IPV6
NETWORK ACCESS CONTROL LIST (Network ACL)
Like a Firewall on subnet level to control traffic
- Stateless
- Subnet Level Security
- One NACL per Subnet
- Support: Allow/Deny
- Block request entering or exiting subnet
NACL Rules
- Order
1-32766 (high, low) - First rule match drive the decision Allow/Deny
- Last Rule is Deny all(*).
- Add Rule in Increments of 100
DEFAULT NACL: allows all traffic in & outNew CUSTOM NACL: deny all traffic until specified which traffic to allow
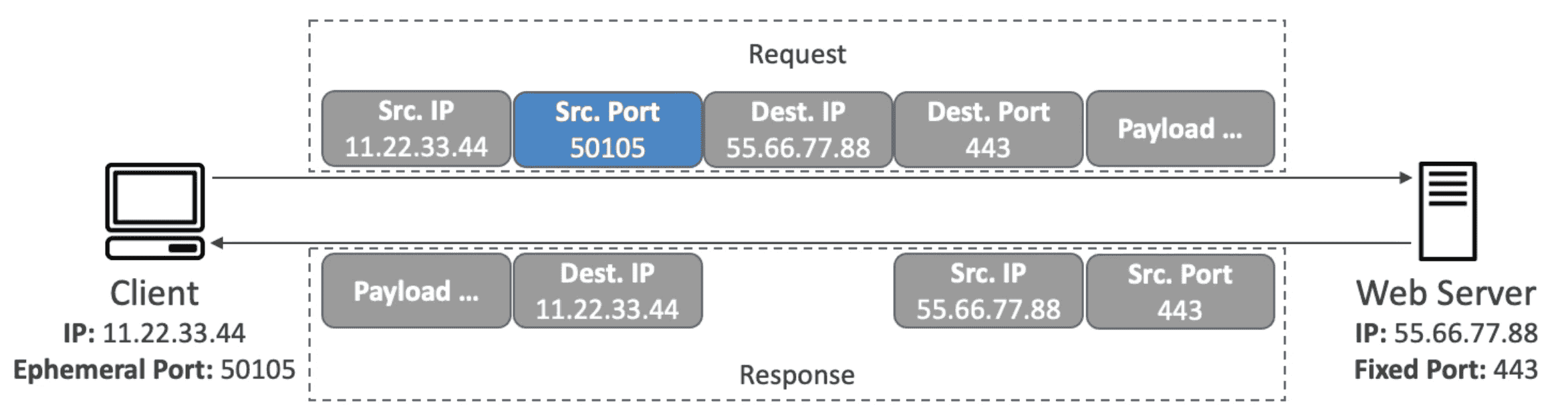
Ephemeral Port
Random Port used by Client to Connect to Fixed port on Server
SECURITY GROUP
- Stateful
- EC2 Instance level Security
- Support: Only Allow
- Outbound traffic allowed by default inbound traffic allowed after check.
- All EC2 Instance are assign to security group
- By Default Security Group block all requests
- Security rules must modify to allow specific type of traffic eg HTTPS
VPC EndPoint
Allow to Connect all AWS service using Private Subnet
- Give better Security and low Latency
- Does not go through public internet
- Scale Horizontally
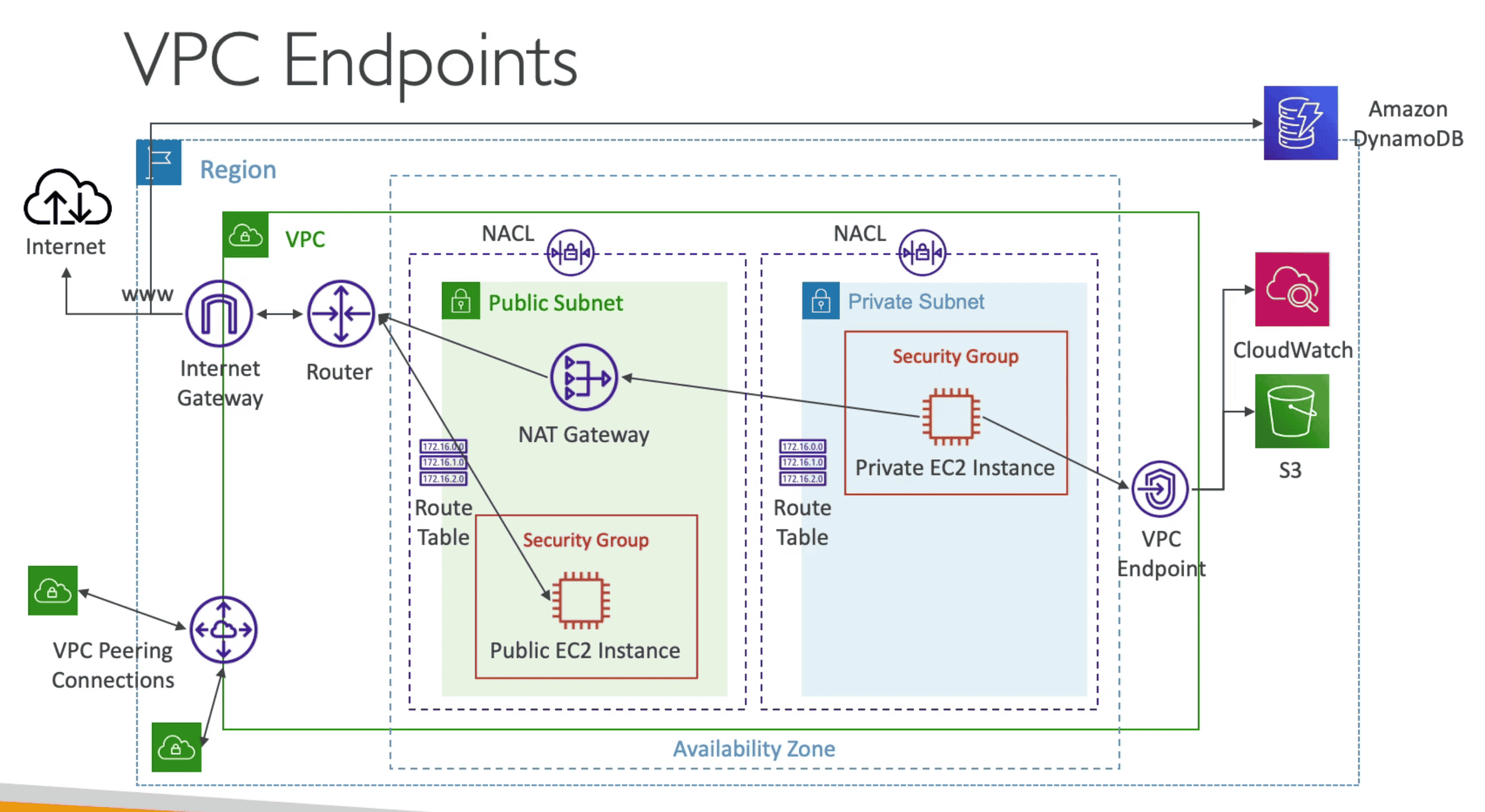
1. VPC Gateway Endpoint:
Connect Only
Dynamo DB & S3
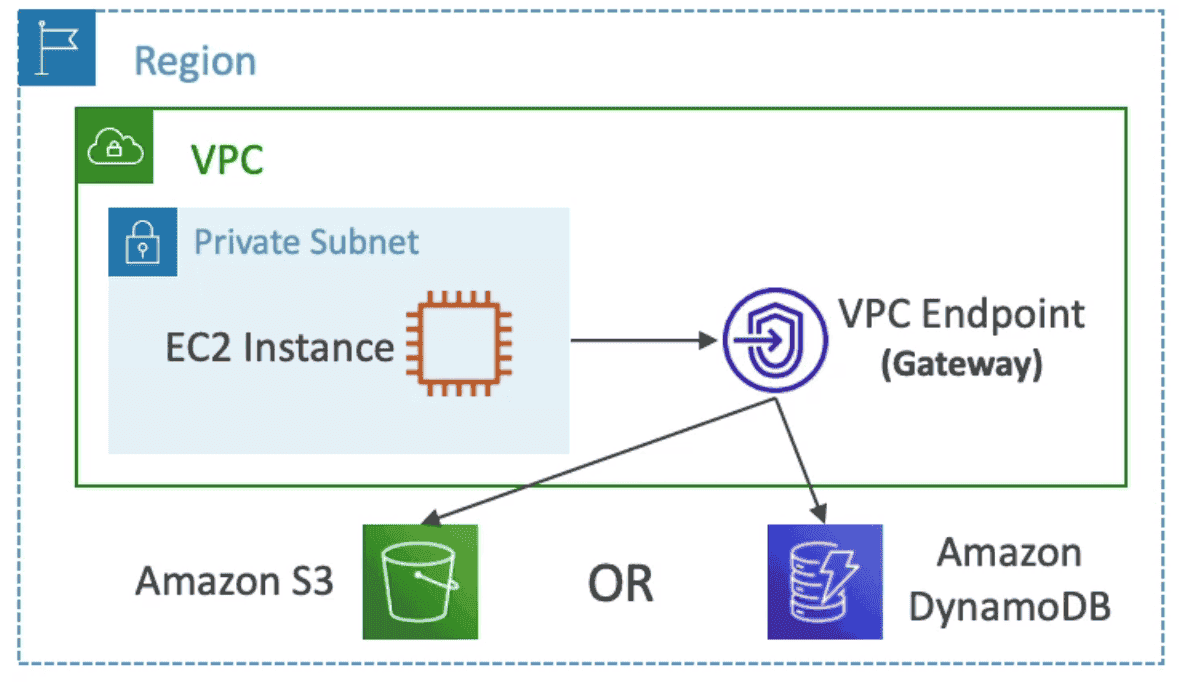
2. VPC Interface Endpoint:
Connect with any other AWS service
- Provision ENI to give entry point for AWS
PrivateLink
Expose a Service to 1000s of VPC
- Most secure & scalable way
- Require Network load balancer on Service side & ENI on consumer side
- Connection goes over AWS Private Internet
- Scale to Multiple AVZ if ENI & NLB is in multiple AVZ
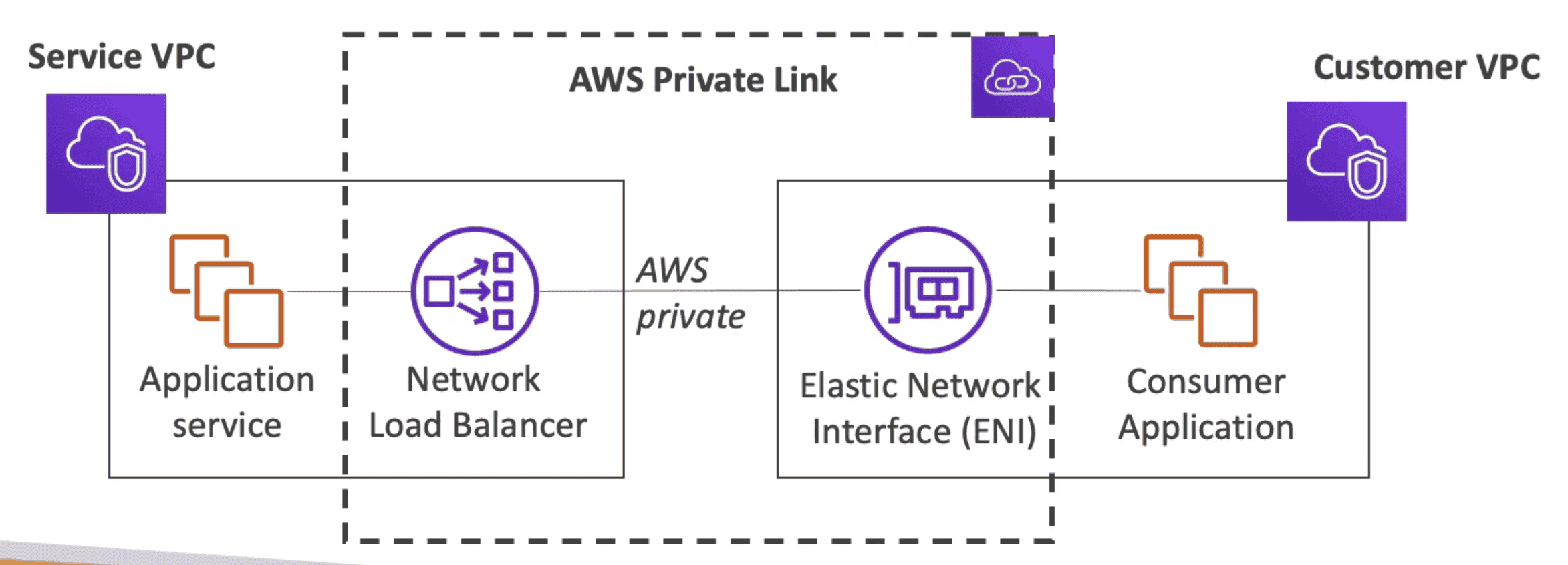
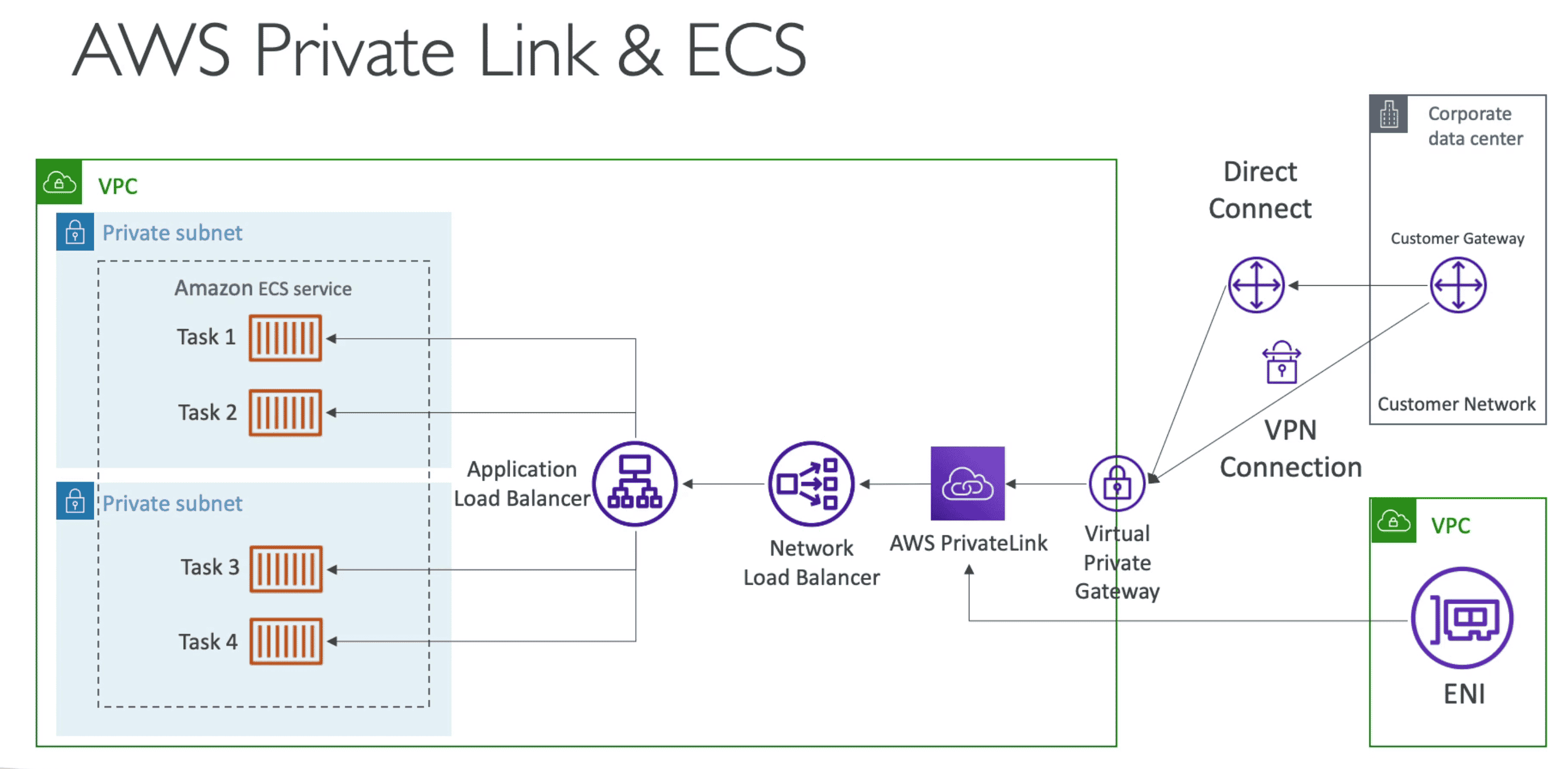
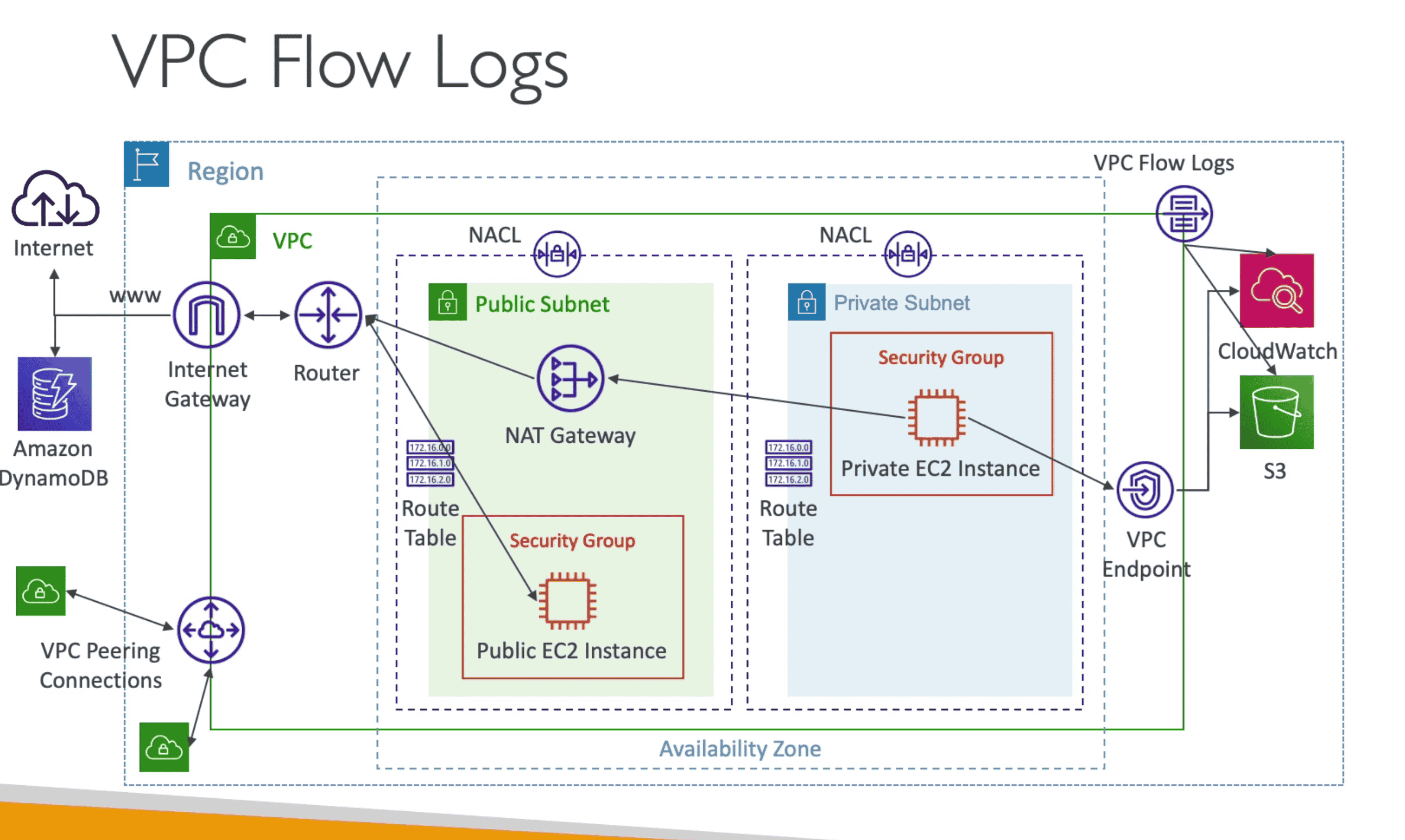
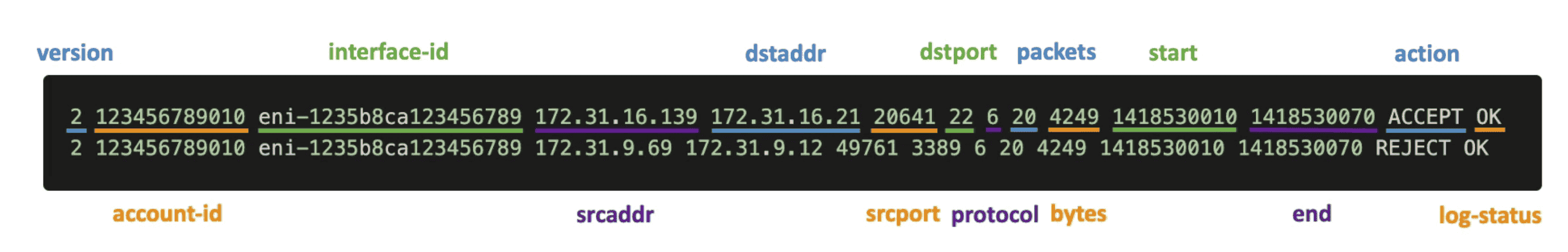
VPC Flow Log
All the Traffic flow logs in VPC
- Help to Monitor & Troubleshoot connectivity issues
- Can be exported to Cloud watch or S3/ Cloudwatch Logs
- Query VPC FLow logs using Athena or CloudWatch Logs Insight
VPC Traffic Mirror
Mirror Network Traffic for analysis in non intrusive manner
- Capture all packet and analyze traffic
- Source & Target should be in same VPC
VPC Reachability Analyzer
Diagnostic tool to check connection between 2 end point
- Analyze Network configuration without sending any packet
On Premises Data Center to AWS VPC
Ways to connect Data Center with AWS VPC
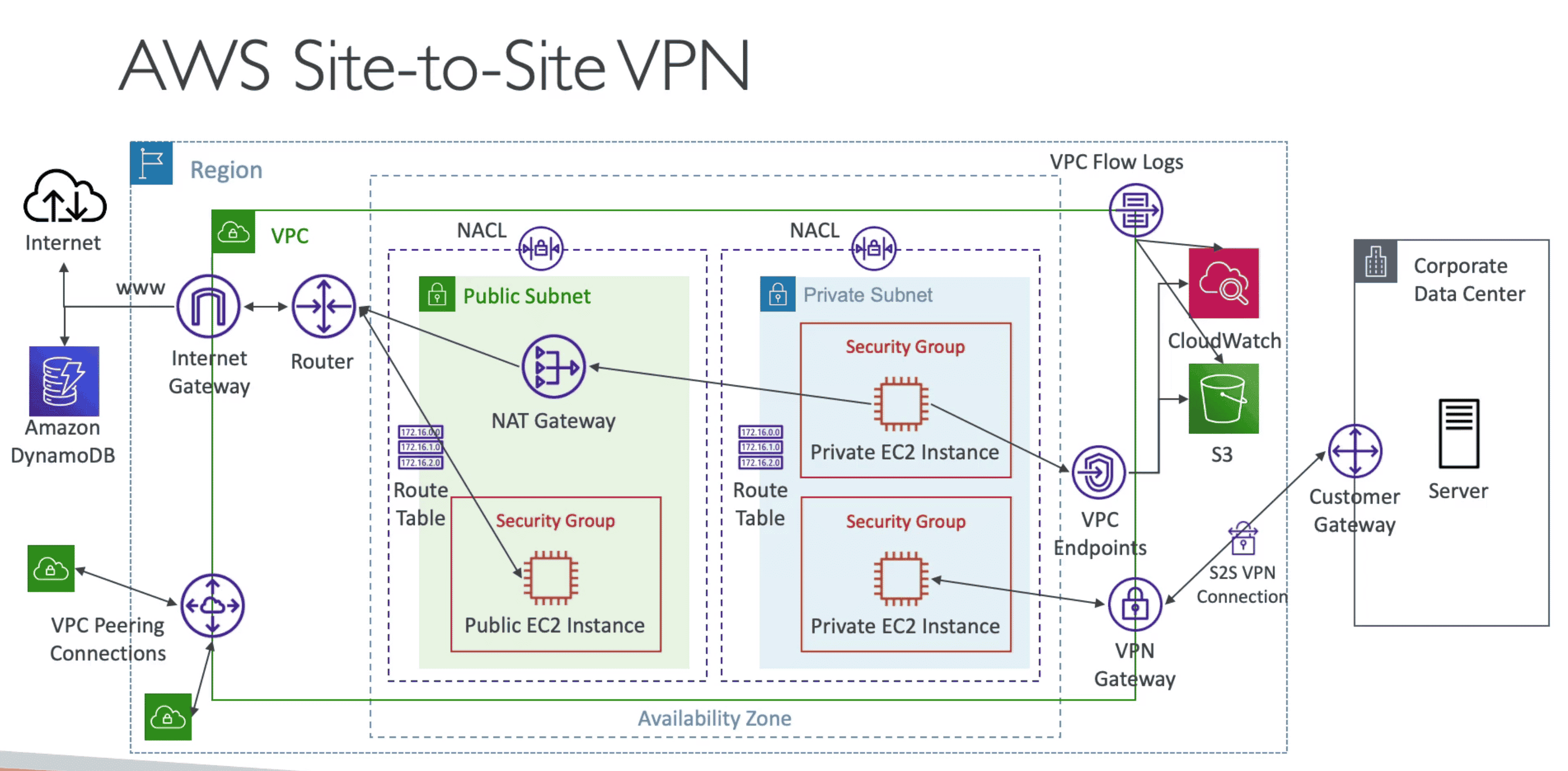
1. Site to Site VPN
VPN Connection with AWS VPC
- Goes over public internet
- Quick Setup in a Minute
- Slow down due to shared bandwidth of internet.
- Connect CGW with VGW
- Route Propagation must be enabled on VPN to enable VPN
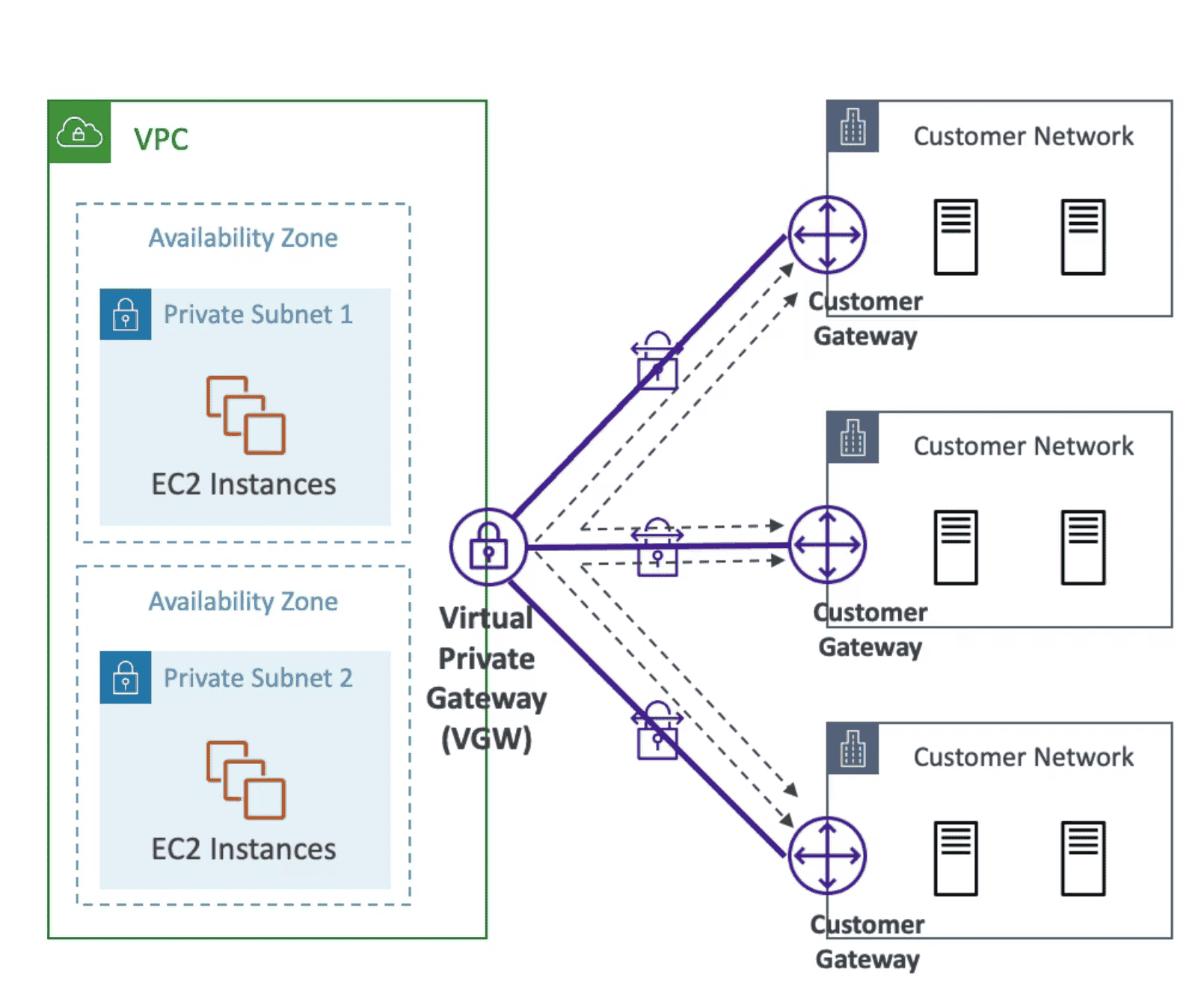
Virtual Private Gateway(VGW)
VPN on AWS Side
- Created and attached to VPC
Customer Gateway(CGW)
Software of Hardware on Client Side
- Can be connected with Private IPV4 or public IPV4 using NAT Device
ICMP Protocol
- Used to ping EC2 instance from on Premises.
- Must be enabled in Security Group to allow Ping from Internet
VPC Peering
Connect 2 VPC privately using AWS network to create unified network of 2 VPC
- Ip Address must not overlap
- Not transitive
((AB)C) != (A(BC)) - In order to connect 3 network we need to connect
(AB)(BC)(CA)) - Can connect cross account/region
- Route tables must be updated in both VPCs that are peered.
CloudHub
Connect Multiple Sites together using VPN
- Connection goes over Internet
- All sites can communicate with each other
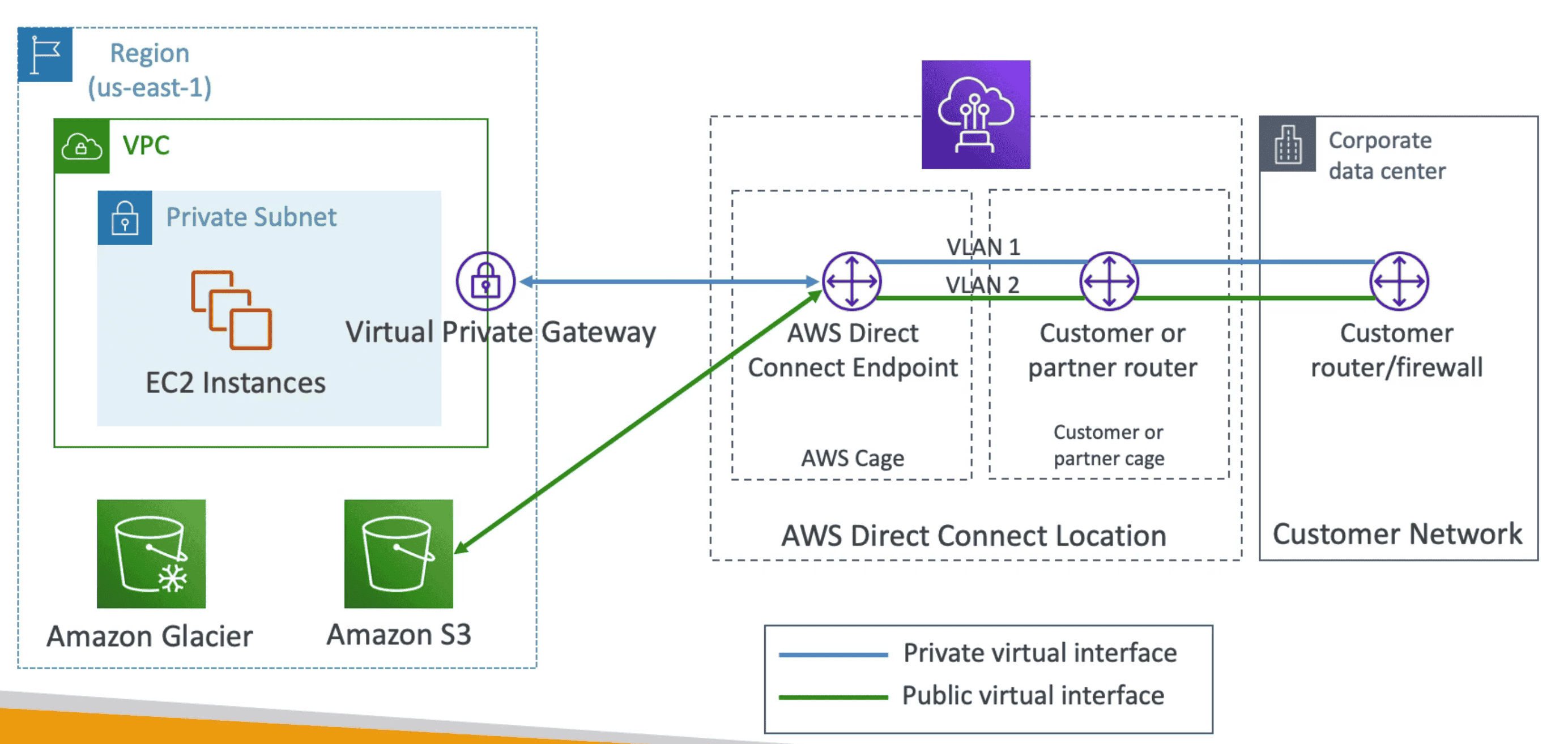
2. AWS DIRECT CONNECT(DX)
Dedicated Private Direct Data Connection from Data Center to AWS.
- Take 1 Month to setup
- Highest speed with highest security.
- More reliable and more secure
- Need to setup VGW on VPC
- Can access Private & Public resources on AWS with same connection.
- Connect on premise server with AWS Direct DX which connects with VGW of VPC
- Data is not encrypted. To add encryption need to add a VPN.
- Maximum Resiliency: Use 2X DX Lines on 2 Location for critical Work Load
- High Resiliency: Use 1X DX Line on 2 Location for critical Work Load
Connection Type
-
Dedicated Connection: Dedicated Port with speed 1-10Gbps
-
Hosted Connection: Shared connection by AWS Connection Partner with 50Mbps, 500Mbps, 10Gbps
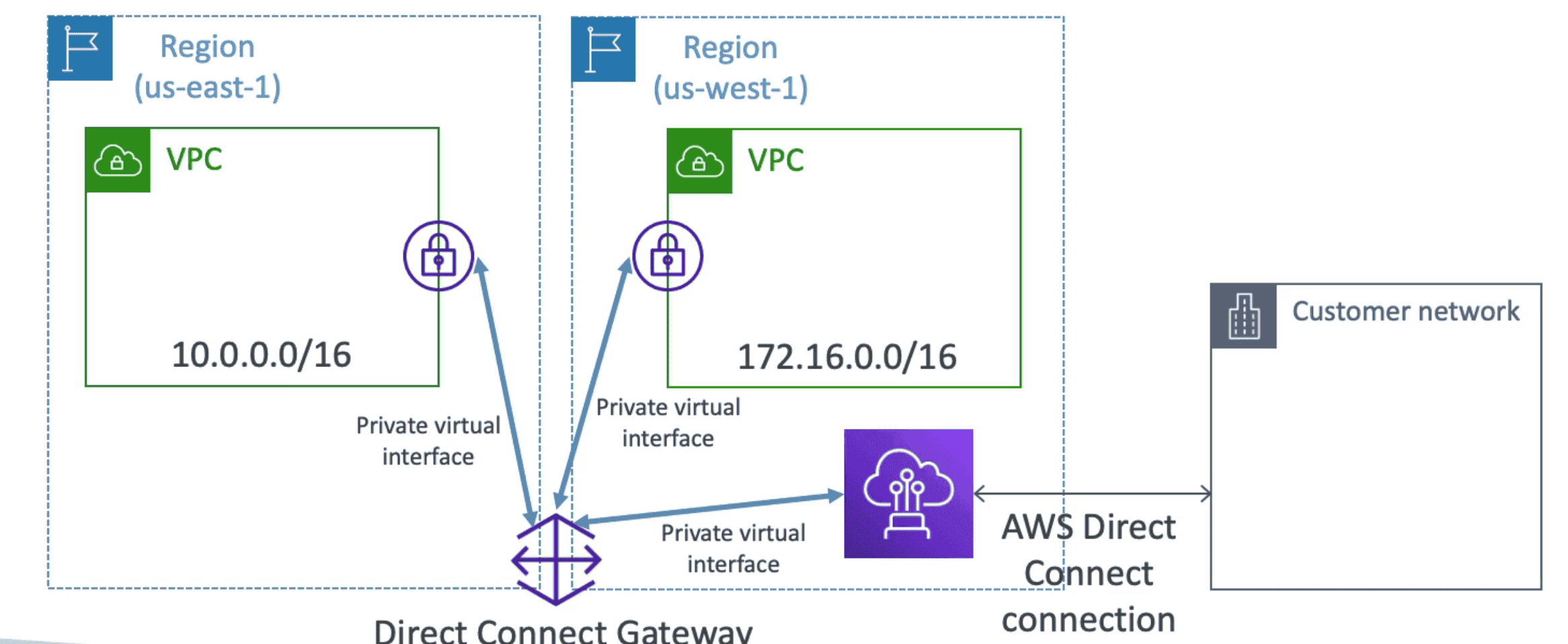
Direct Connect Gateway
Connect multiple VPC from different region using Direct Connect
- DX Gateway connect multiple AWS VPC with DX Location.
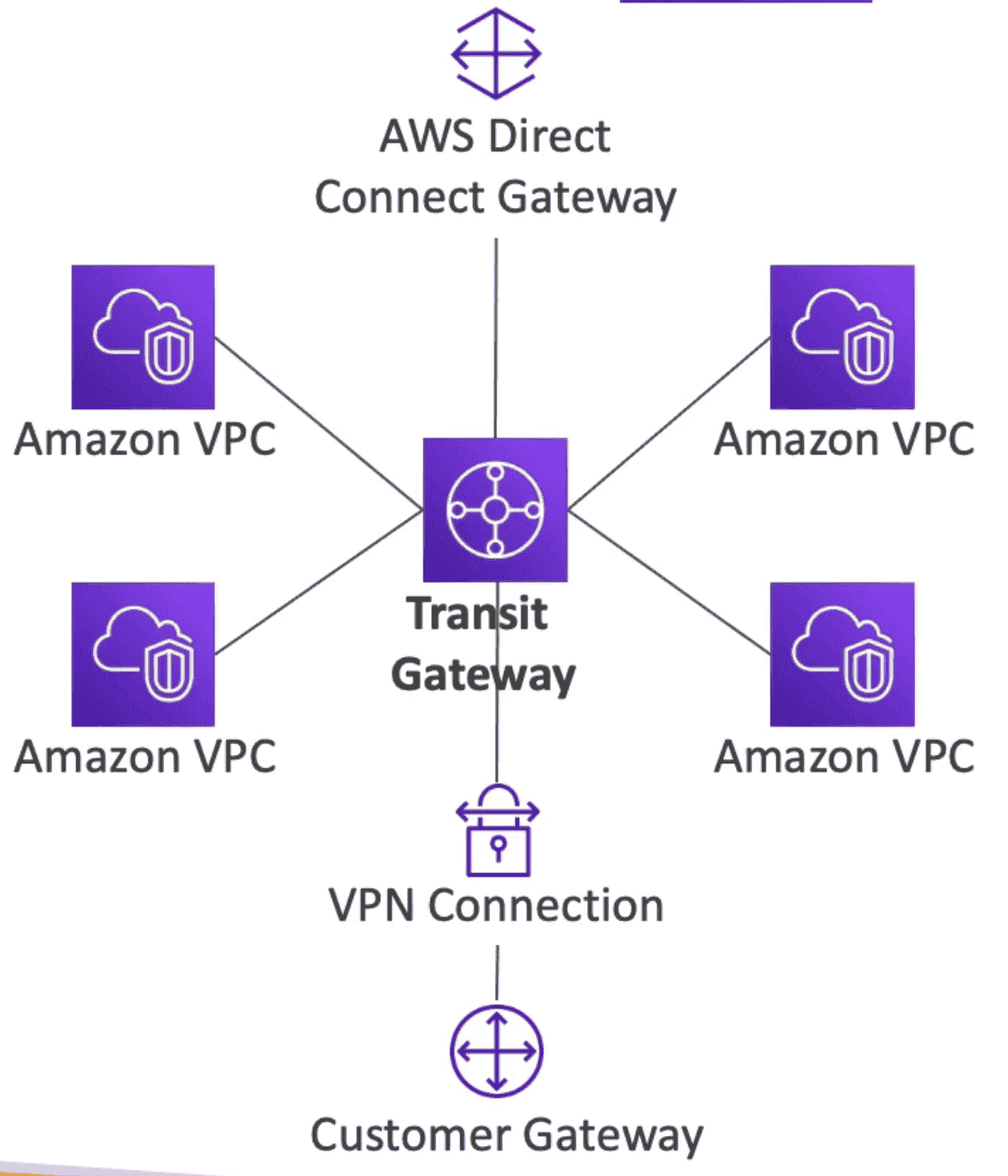
AWS TRANSIT GATEWAY
Peering Confection with On premise Data Center with Hundreds of Thousand of VPC, Direct Connect
- Works on cross region
- Help simplify Network Topology
- Possible to peer Transit Gateway across regions
- Route Table: to define traffic
- Only service support
IP MultiCast
ECMP(Equal Cost Multipath Routing)
Allow Multiple site to site vpn to increase Bandwidth
- Site to Site VPN : 1.25 Gbps
- 1XECMP = 2.5Gbps
- 2XECMP= 5gbps
