Security
Shared Responsibility Model
AWS responsible for Security OF the Cloud
Customer responsible for Security IN the Cloud
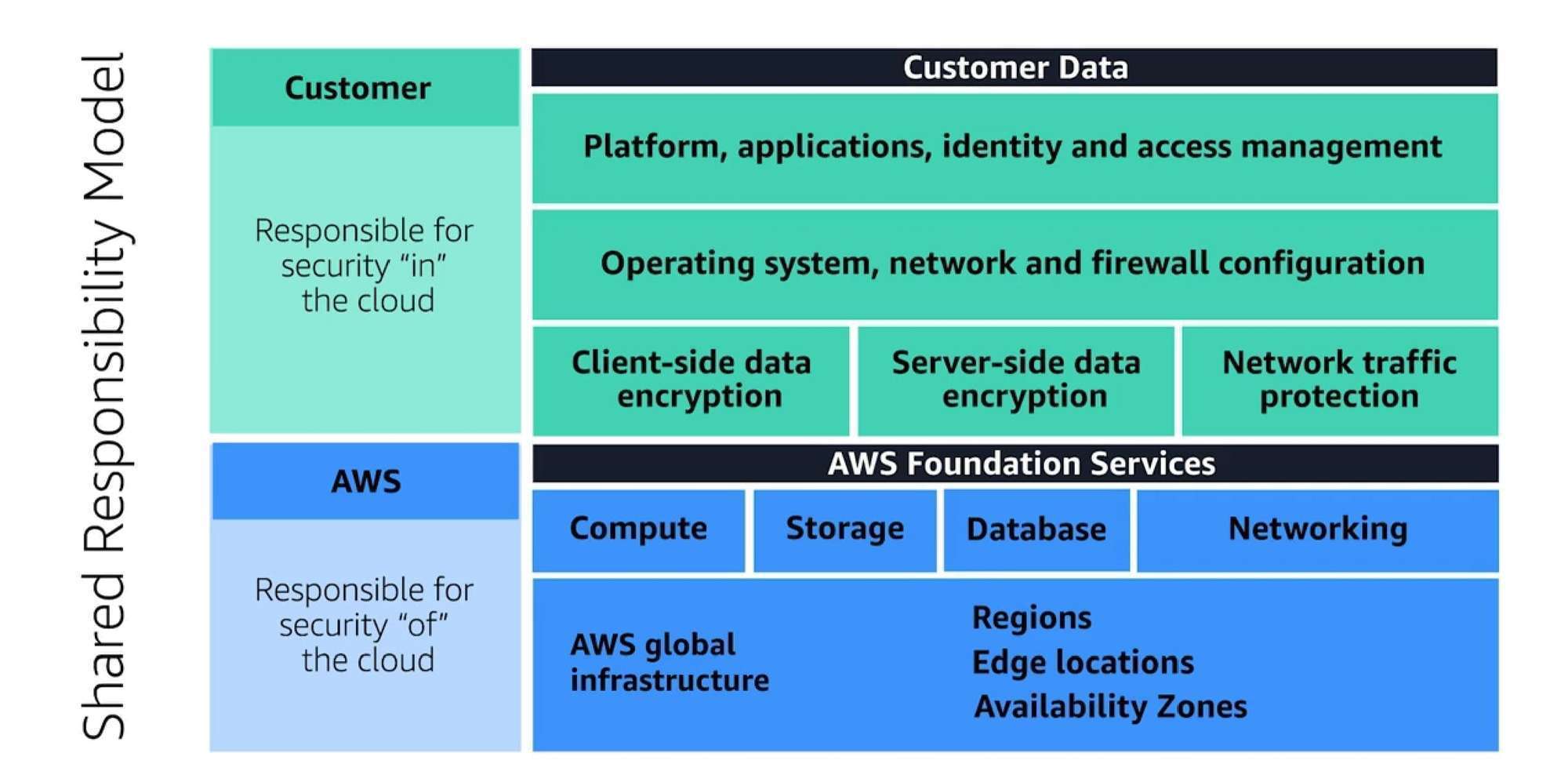
AWS Responsibility:
responsible for security of the cloud.
- Physical Layer
- Network Layer
- HyperVisor Layer
- Manged Services: S3, DynamoDB,RDS etc
Customer Responsibility:
responsible for the security of everything that they create and put in the AWS Cloud.
- OS Root Access & Security Patch for OS
- Application Layer Security
- Data Security
- IAM Access Management
- Encryption of Data
AWS Identity and Access Management (IAM)
Global Service to manage users and their access
Principle of least privilege:
Granting only the permissions that are needed to perform specific tasks
Root user
- Owner of AWS Account
- Full control of AWS Account
- Complete Access & Control any Resource you want.
- Multi Factor Authentication (MFA) must be used to login
Only Root user can perform Actions:
- Change Account Setting for Root User
- View Certain Tax invoices
- Close AWS
- Change/Cancel AWS Support Plan
- Restore IAM user permission
- Register as seller in AWS marketplace
- Sign up for GovCLoud
- Edit Delete S3 Bucket policy
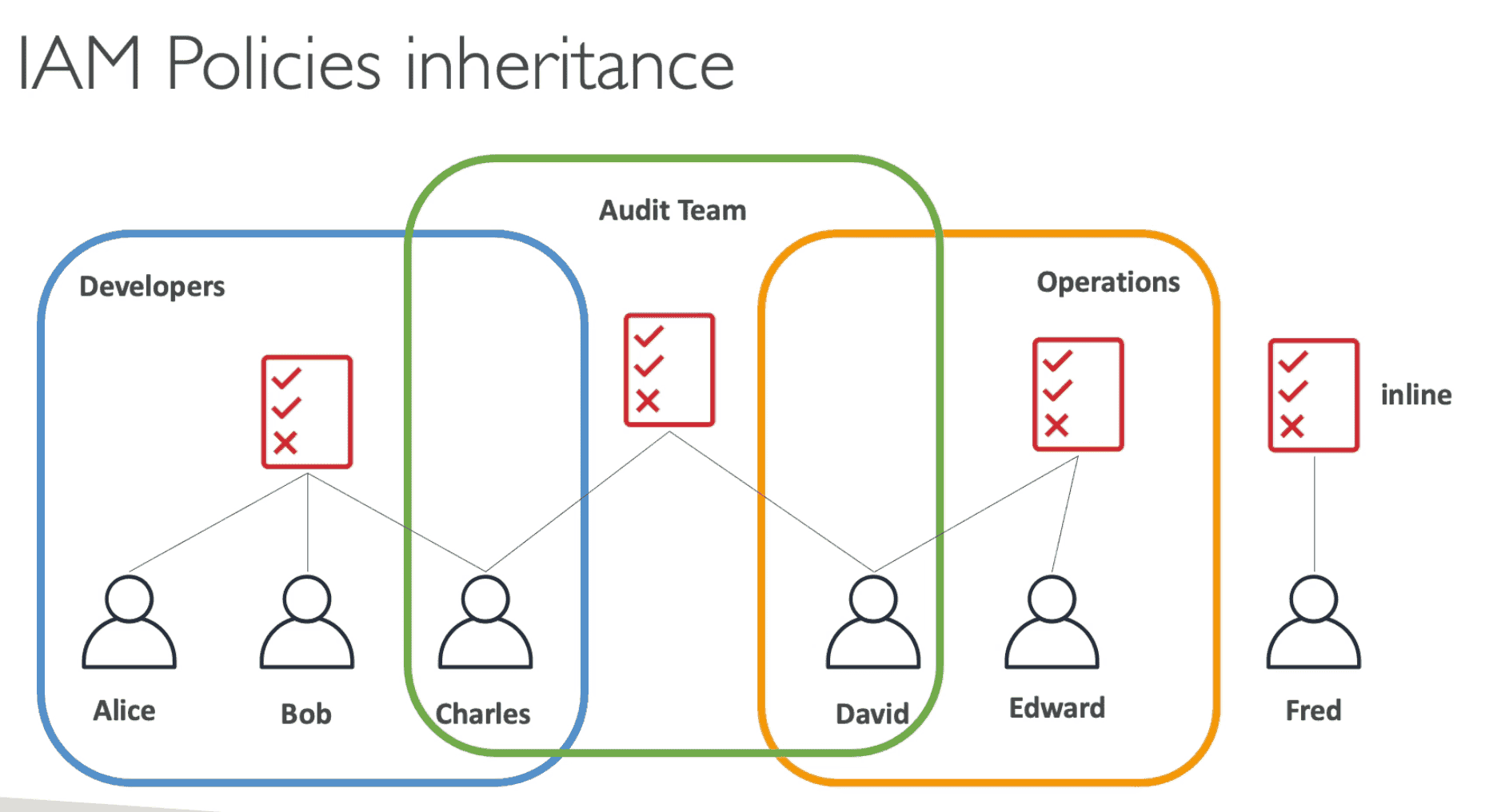
IAM users
- 0 permission by default. Can't even login to AWS until given permission
- Grant permission to AWS service by IAM Policy
- Explicitly give permission for each Action
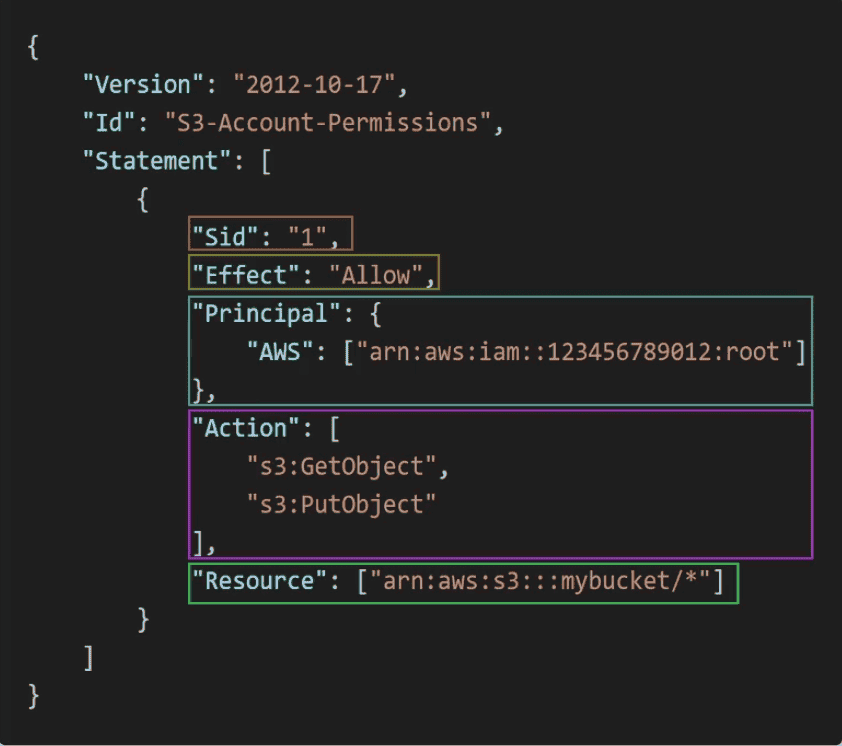
IAM policies
JSON state which AWS services IAM user/ IAM Group/ IAM ROle can access
- For S3 Buckets, Bucket Policy along with IAM Policy need to be considered.
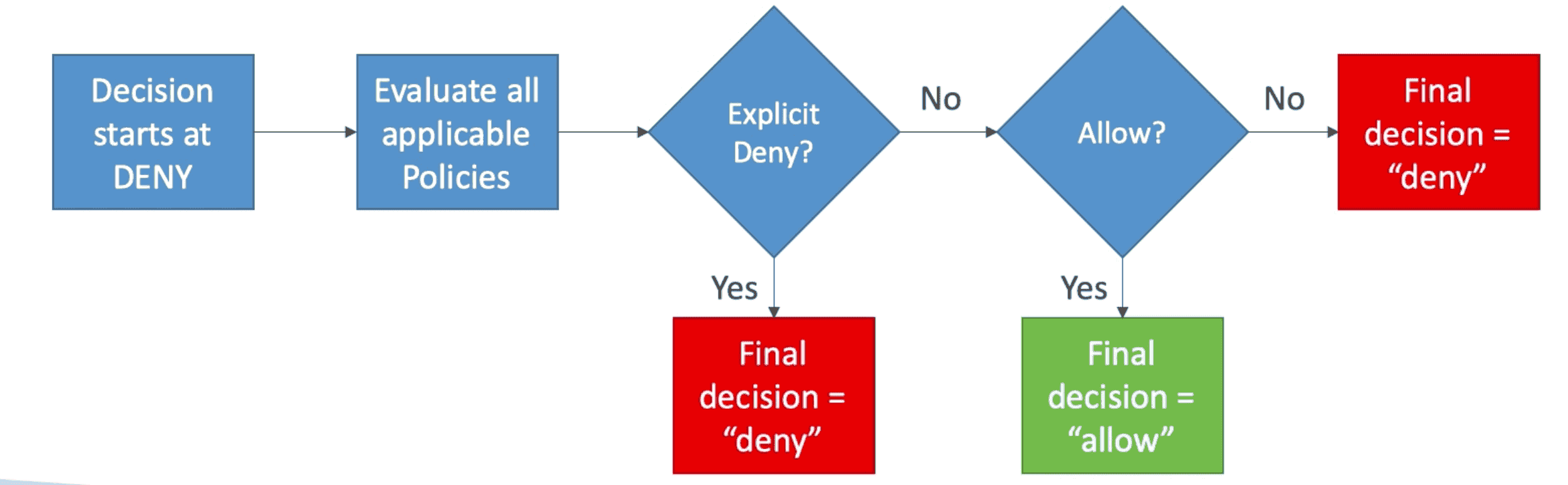
IAM Authorization Model
- Any Explicit Deny--> DENY
- An Allow--> ALLOW
- Else-->DENY(Default)
Inline Policy
Policy added on top of other policy inline for a role
- One to One relationship of user-policy
- Deleted along with user
Policy Generator
Visual editor to generate Policy
Policy Simulator
Simulator for Policy access validation
Structure
- Version Number: Version of Policy
- ID(Optional): Identify policy
Statement:
Define;Action/scan be performed byPrincipalonResourcesas anEffect
- SID(Optional): Statement ID identify the policy statement
- Effect: Allow/ Deny as effect of policy
- Principal: Account/User/Role Policy apply to
- Action: List of API Calls
- Resource: List of Resources
- Condition: condition when Policy apply

IAM Group
- Assign IAM Policy to a Group of IAM Users
- Only contain IAM Users not other Groups
- Multiple Group can belong to IAM Users
IAM Role
Temporary grant access to resource, users, apps, other aws services https://console.aws.amazon.com/iamv2/home#/roles
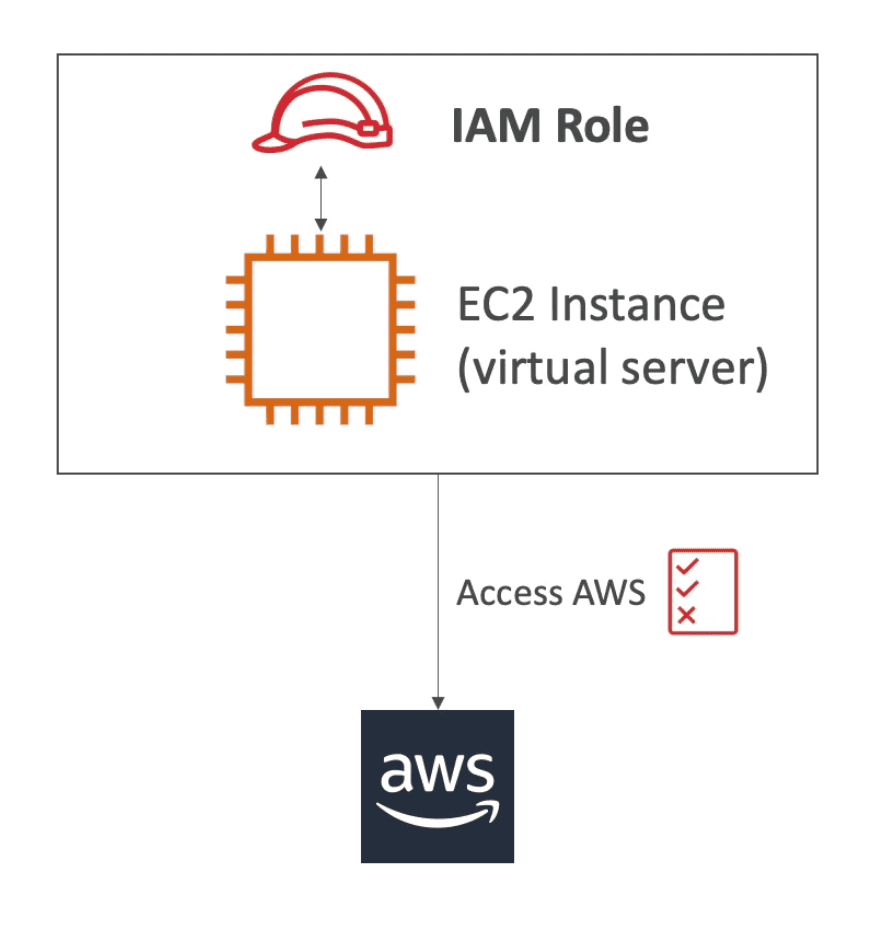
- Allow/ Deny Permission to services to call other service on your behalf
- No username or password, ACCESS KEY is assigned dynamically
- Used by other AWS services
- Common Roles:
- EC2 Role
- Lamda Role
- Cloud Formation Role
Within AWS use IAM Role as much as possible
- EC2 Instance Role for EC2 Instance
- ECS Role for ECS tasks
- Lambda role for Lambda Function
Outside AWS
- Use Environment Variable
- Named profile using cli configure for multiple account setup
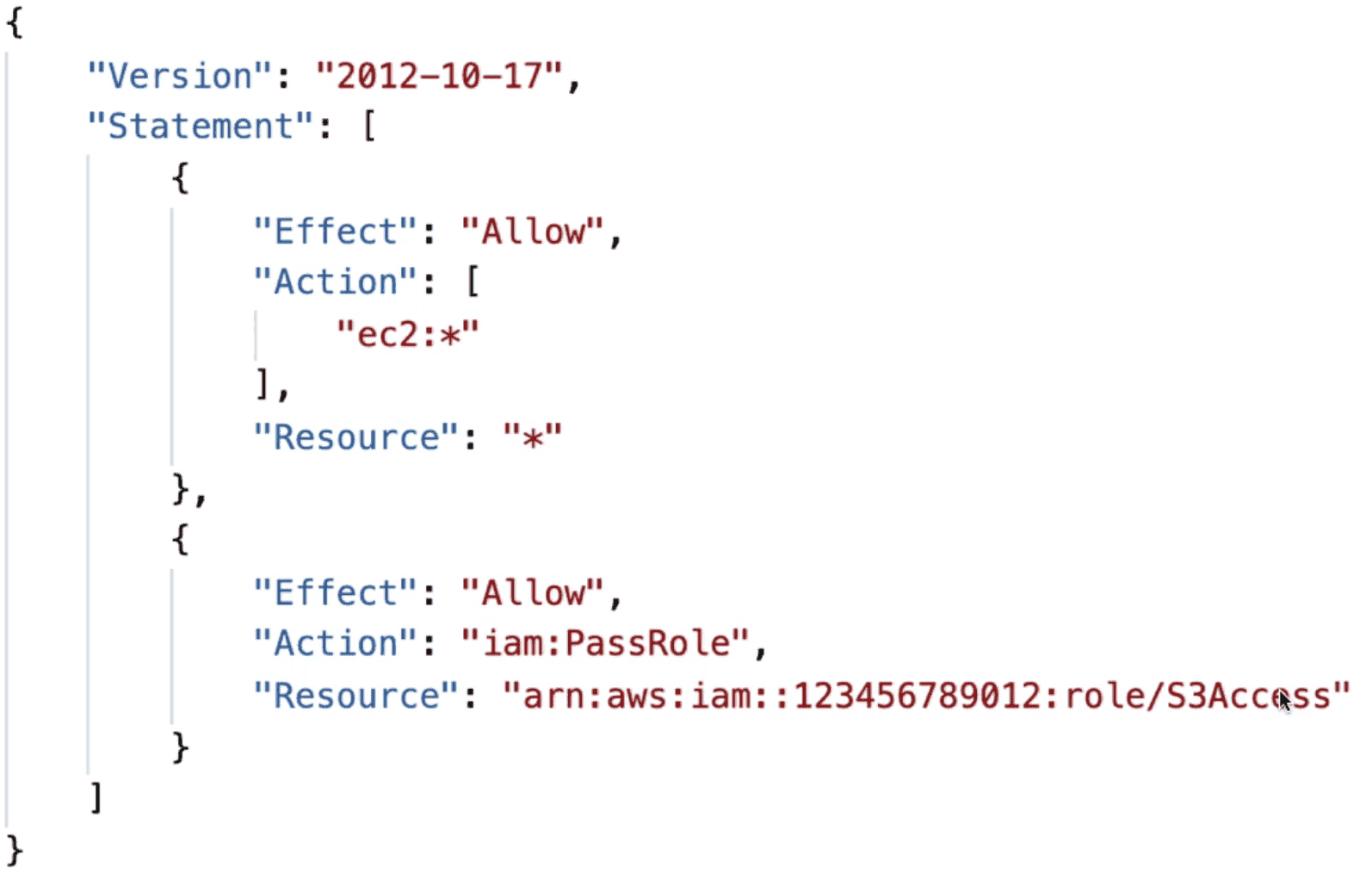
Permission needed to pass role to other service
iam:PassRole: IAM permission to pass roleiam:GetRole: View Role being pass
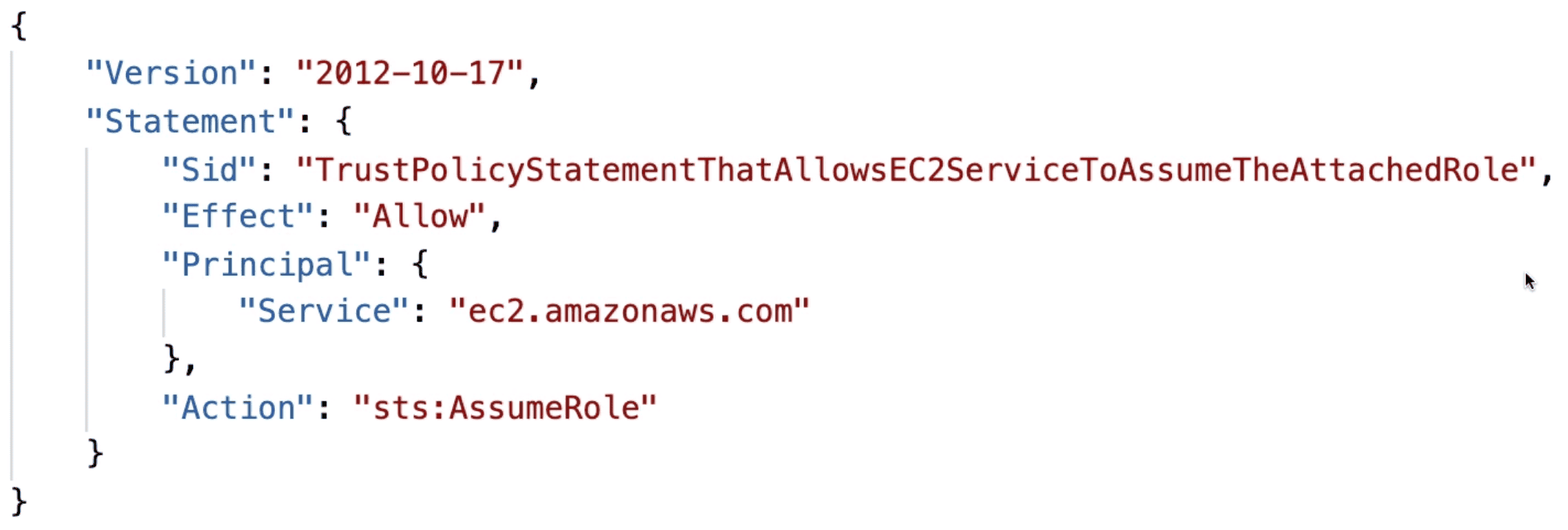
trustpolicy: Role can only be pass to a service which is defined in trustpolicy
Password Security
ACCESS KEY
-
SDK & CLI need to access AWS cloud using ACCESS key
-
1. AWS Management Console
Browser Based tool used for testing & learning
-
2. SDK (Software Development Kit)
Developer can use API in various languages
- JS, C++, Java, .NET, NodeJS, PHP
- Embed within App & IOT
-
3. CLI (Command Line Interface)
Used for Automation script in Windows, Mac & Linux.
- Direct access to AWS Public API
- Open source
AWS CloudShell
Execute Command directly on cloud
- Free to use
- Come with 1GB storage to persist Script
- Download/ Upload Files
- Not available in all regions
Set AWS Password Policy
- Set Policy on user password
- Allow user to set password
- Force user to change password
- Prevent reuse
MFA Multi Factor Authentication
Password + Security Token
1. Virtual MFA Device :
software app that runs on a phone
- Google Authentication(Phone Only), Authy(Multiple Device)
2. UTF/U2F Key (Universal Second Factor Key):
device that you can plug into a USB port on your computer.
- U2F is an open authentication standard hosted by the FIDO Alliance.
- sign in by entering your credentials and then tapping the device instead of manually entering a code.
- Physical Device Yubikey
3. Hardware Key Hub:
hardware generating key
- Gemalto, SurePass from US Governments
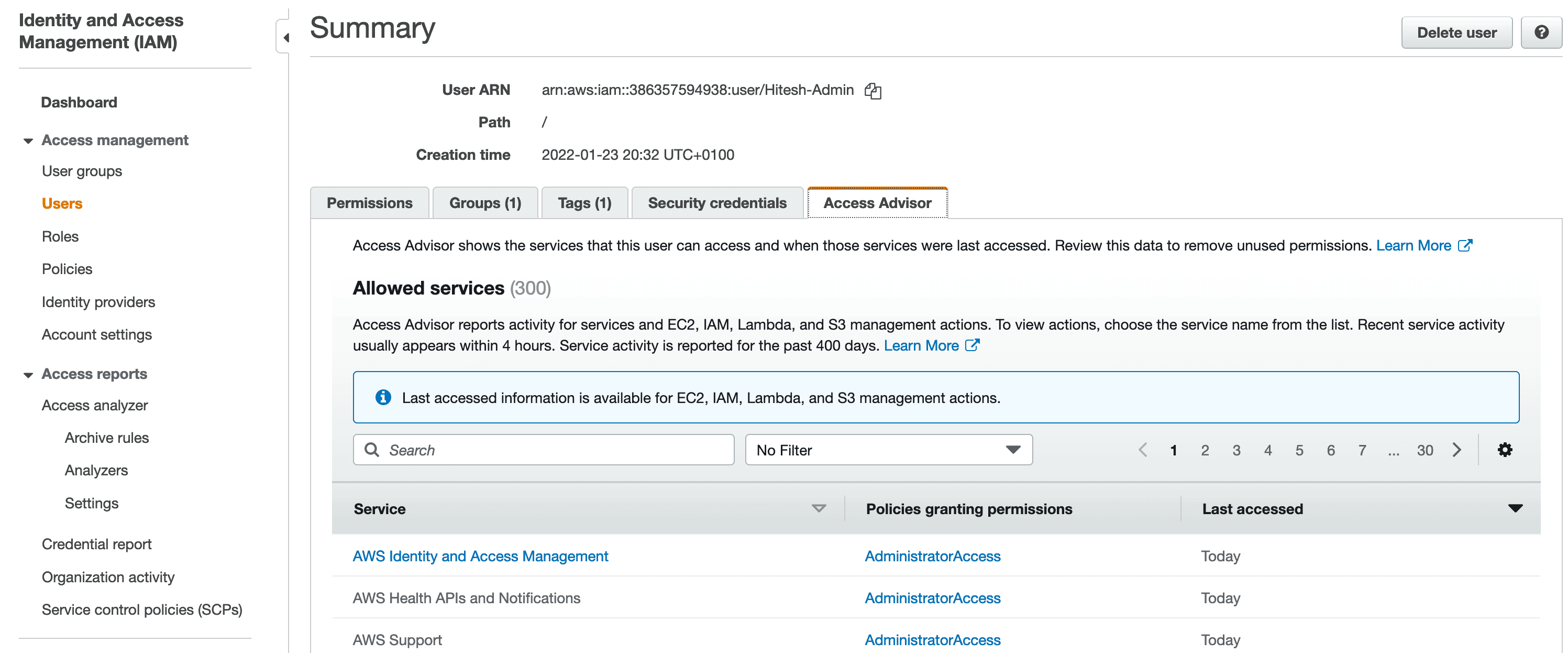
IAM Security Tools
| IAM CREDENTIAL REPORT | IAM ACCESS ADVISOR |
|---|---|
| Account Level | User Level |
| List of user & status of their credential | Service permission granted to user |
| Look at user security | Look at API used by user account to remove service not used by user out of 300 services |
AWS Organization
Group accounts into Organization unit(OU)
- Center Location to Manage all accounts
- Global Service
- Combine billing for all accounts and get discount
- Hierarchal group accounts for security and compliance
- Account creation can be automated with help of script
Consolidated Pricing
- Pay price by combining bill of all AWS Account
- Easier to pay bill because we need to pay bill at single location
- Bulk Pricing Discount on aggregate amount
- Free of cost
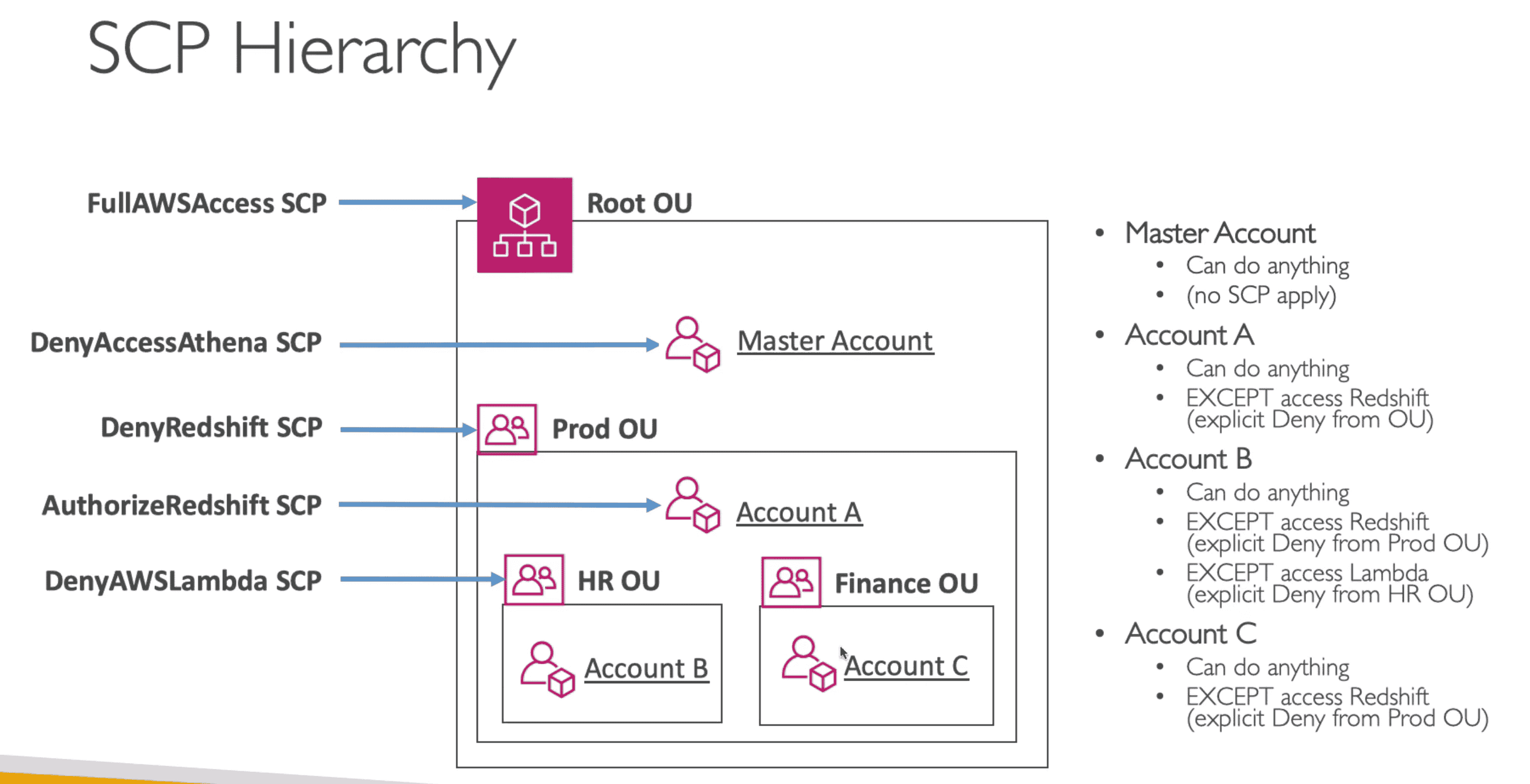
Service control policies (SCPs)
centrally put restrictions on the AWS services, resources, and individual API actions that users and roles in each account & OU can access.
- Whitelist/Blacklist IAM Action in OU
- Apply at OU or account level
- Does not apply at Master Account
- Top Level SCP take preference over account level SCP
- Does not allow by default. Must have a explicit allow
AWS Control Tower
Dashboard to manage all accounts & OU
- Better way to manage organization
- Best practice to create a multi account organization
- Automated setup and free of cost
Accounts:
- Master Account: admin account for billing
- Log Archive account: immutable logs for audit
- Audit Account: Compliance account for Audit
Guardrail: rule to govern OU
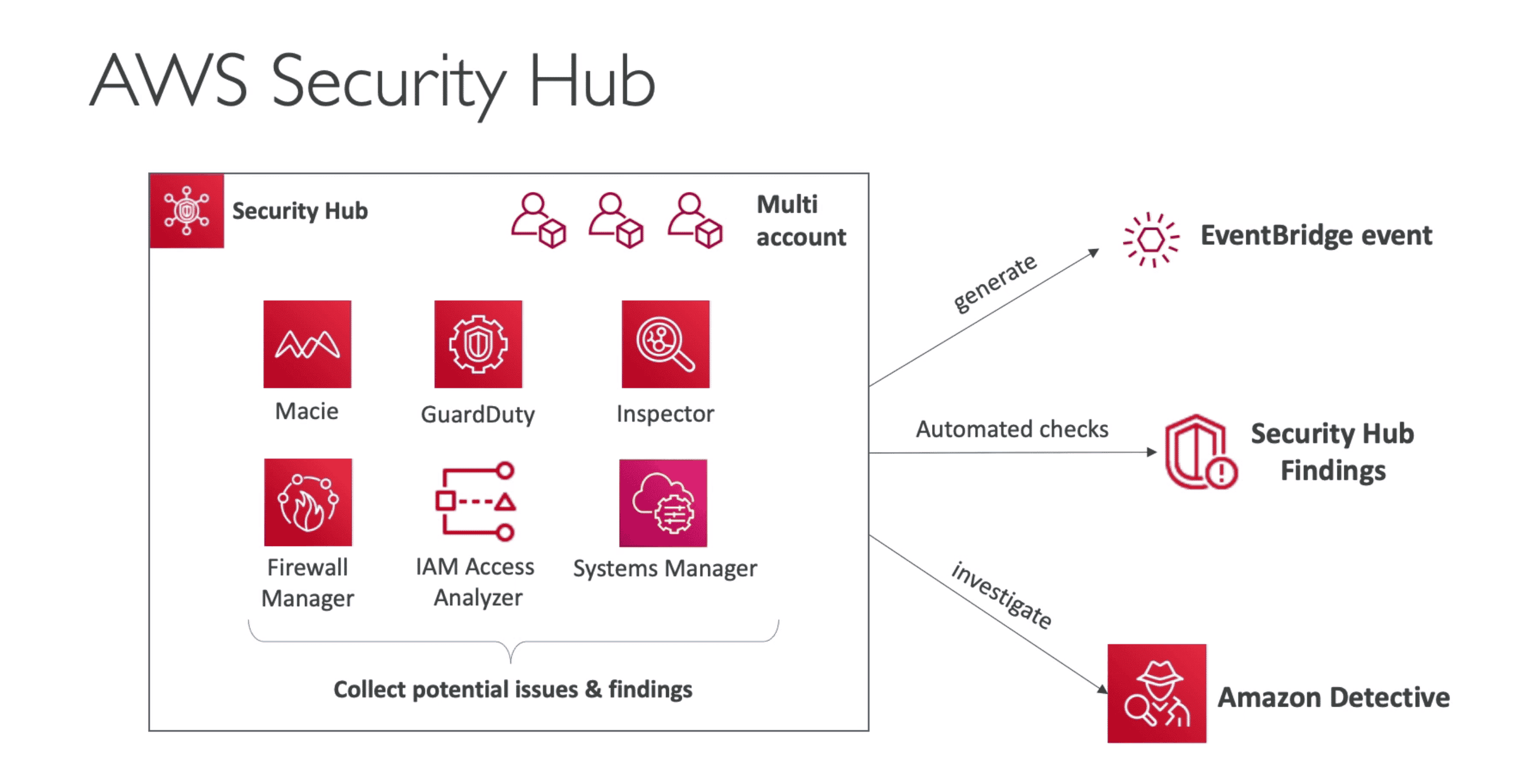
AWS Security HUB
Centralize Hub to show Notification & Action in unified Dashboard
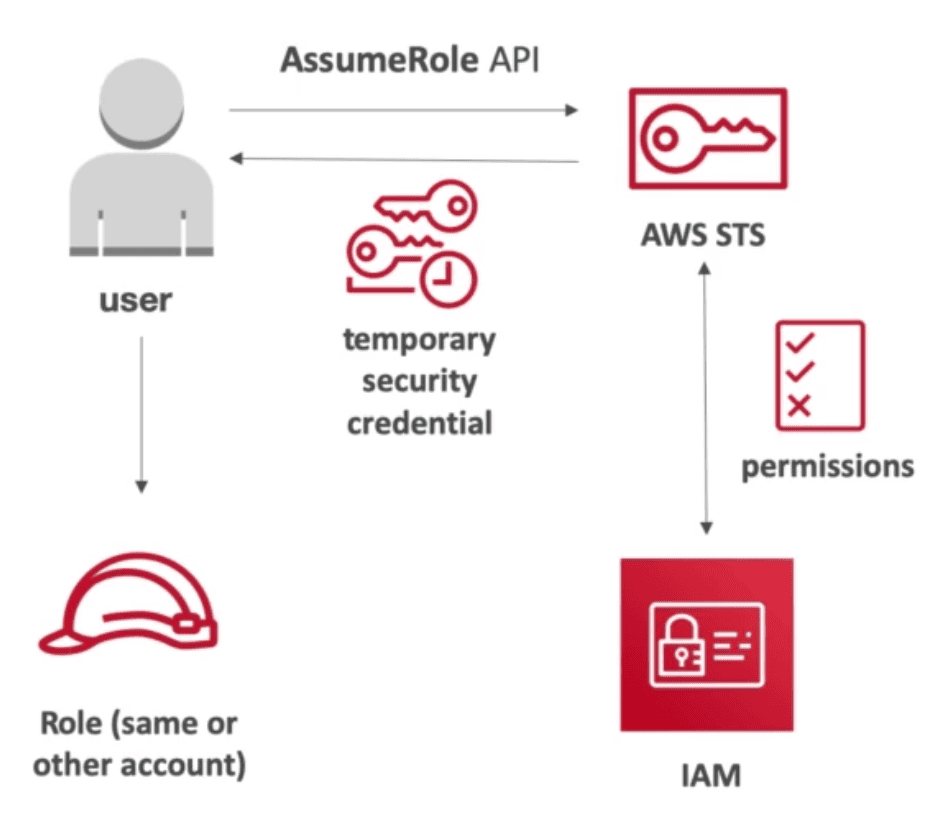
SECURITY TOKEN SERVICE (STS)
Give IAM Role to user with limited & temporary access to AWS resources privilege for
1 hour
- Give short term Security Access & Session key with expiration time valid between 15 Minutes to 1 hour
- Used behind the scene
APIs
AssumeRole
IAM User assume a role to perform some tasks for added security.
-
AssumeRoleWithSAML: using SAML Token to Login as IAM user -
AssumeRoleWithWebIdentity: allow access via facebook, gmail
GetSessionToken:
used to get MFA to get session token Return:
- Session ID
- Secret Key
- Session Token
- Expiry date of Session Token
GetFederationToken: temp credential for federated user
GetCallerIdentity: detail about IAM User & role used in API call
DecodeAuthorizeMessage: decode error message
Identity Federation
User management by third party. AWS trust the Identity form third party eg SAML
Amazon COGNITO
Direct access to external clients from Mobile & Web User
- Preferred over using AssumeRoleWithWebIdentity
- Internal Database of user to create IAM user for Mobile & Web users.
- Identity management for users from login with FB, Google, SAML
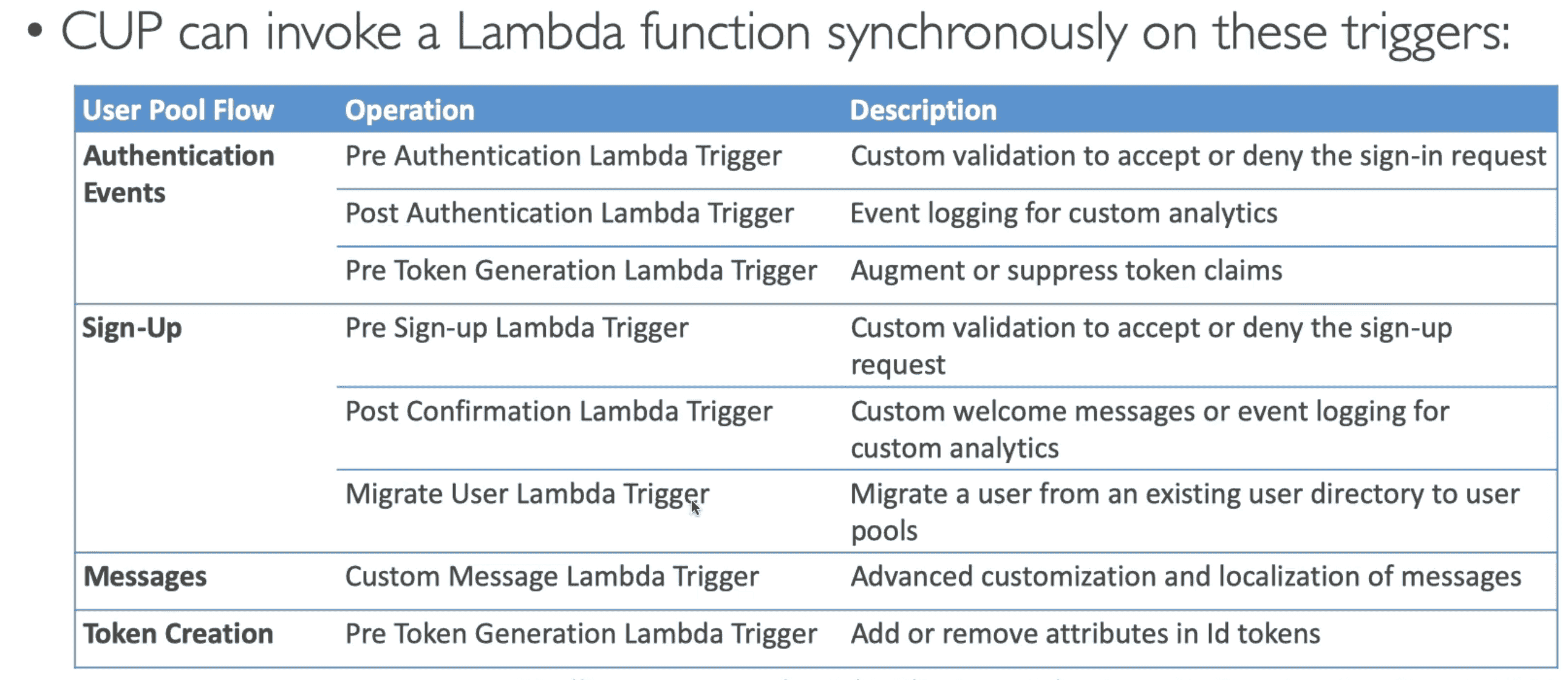
Cognito User Pool (CUP)
Serverless DB of Mobile & Web Users
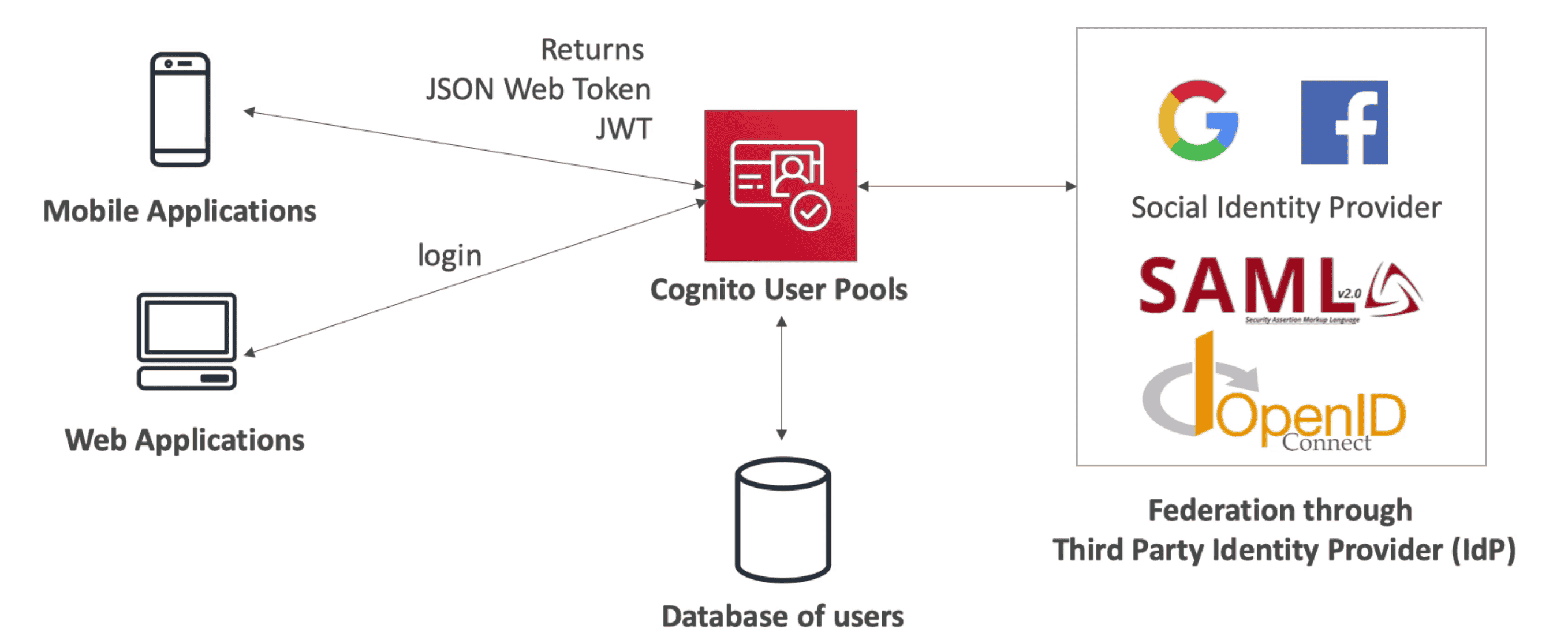
- Allow User to Sign in using email, phone number, gmail, facebook, SAML
- Good for external user management
- Support MFA
- Send back JWT(JSON Web Token)
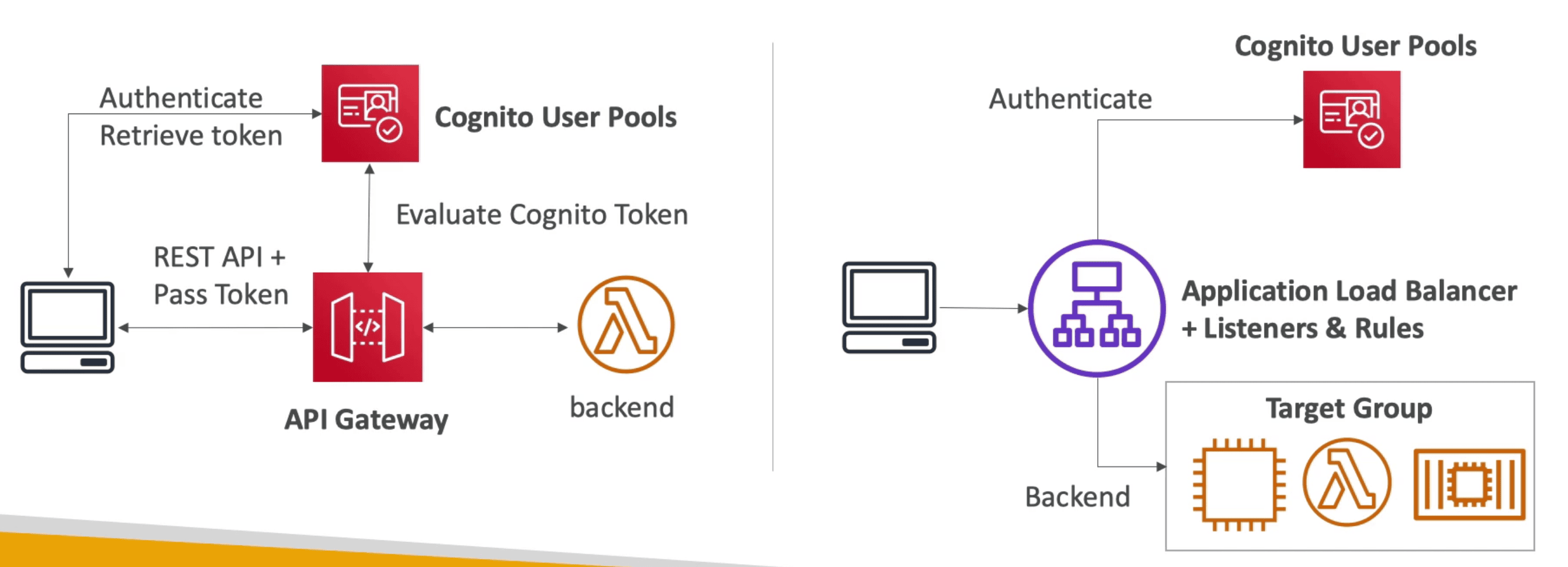
- Provide ready to use Login Page as
Hosted Authentication UI - Integrate with
APIGateway&ALBto Authenticate user on Backend
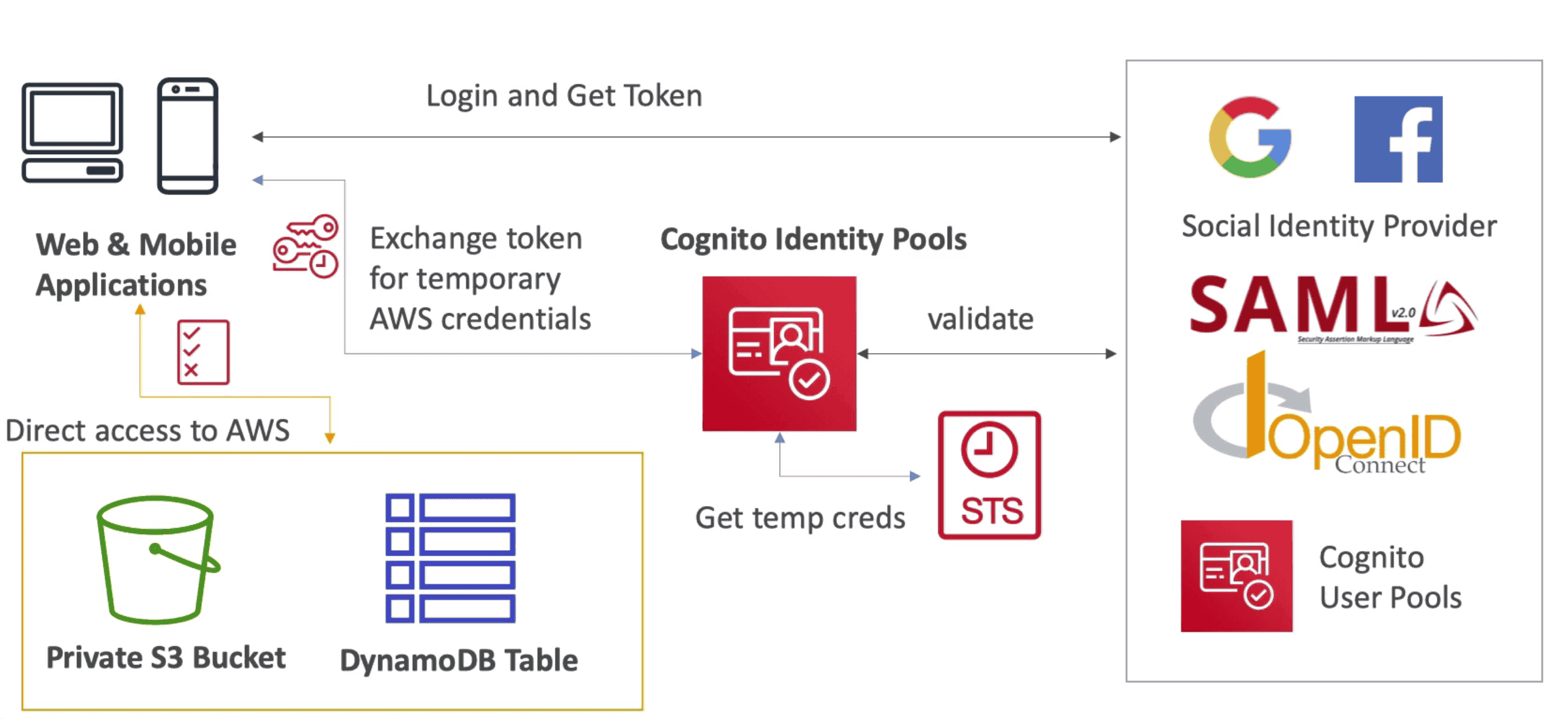
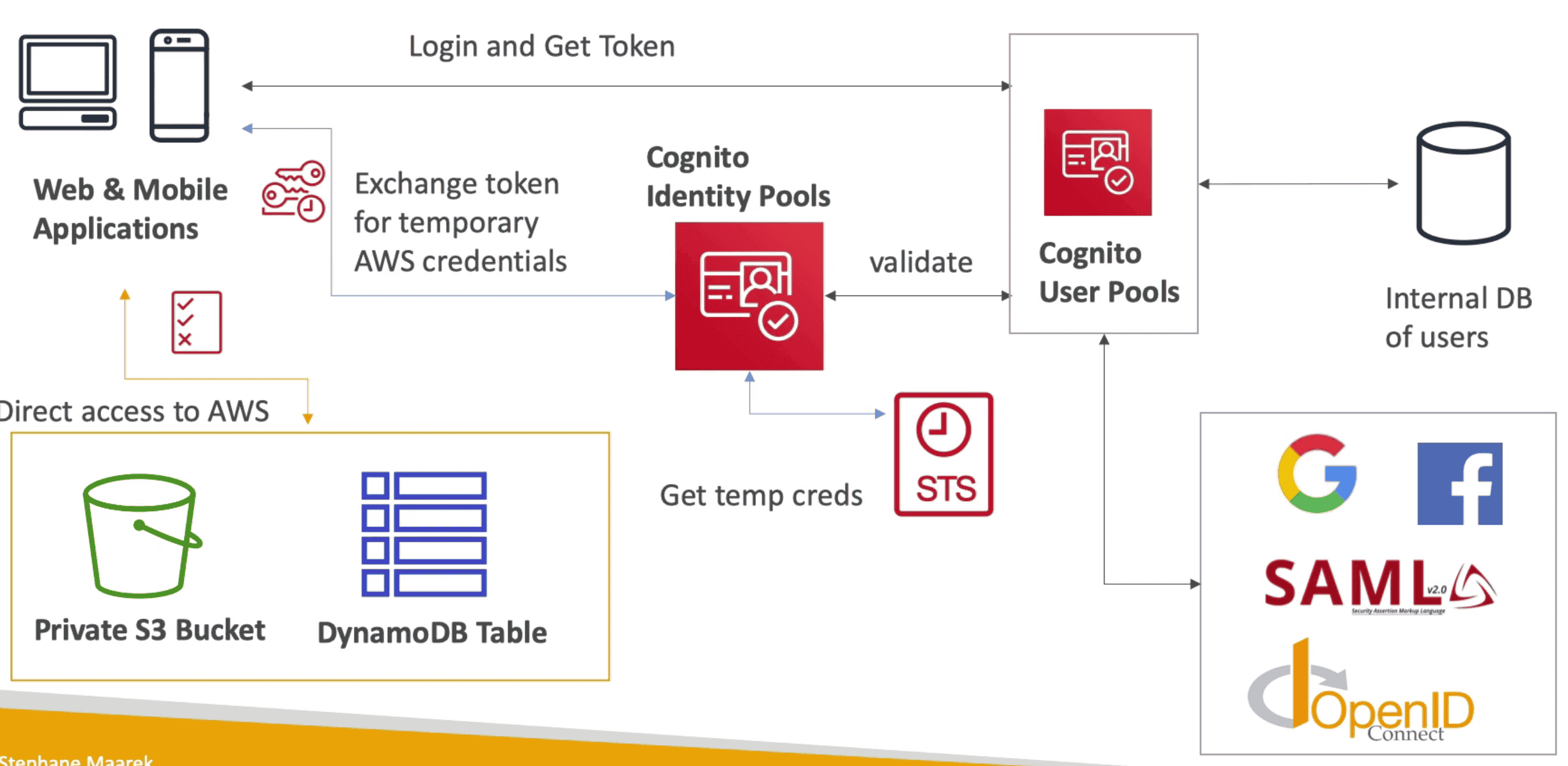
Cognito Identity Pool (FIP)/ Federated Identity
Provide Direct Access to AWS resource for Mobile or Web Users
- Connect with Identity Provider to validate user and give temporary credential with help of STS.
- Identity Source could be
- Cognito User Pool(CUP)
- Public Provider: Google, Facebook, Apple etc
- OpenID & SAML
- Custom Login Server
- Anonymous Guest user
- Provide Temporary Access Token to user using identity provider
- Use Identity Provided by pool to access AWS Service or API Gateway with attached
IAM Role
Using CUP to authenticate
Cognito Sync
synchronize user profile data across mobile devices and the web without requiring own backend.
- Sync preferences, configuration & state from device to Cognito
- Deprecated in favour of
App Sync
Microsoft ACTIVE DIRECTORY SERVICE (AD)
AD Found on Window Server, AD Service help to integrate AD on AWS
- DB of Objects with Centralized security management
- Objects are group as Tree and Tree into Forest
- Manage user Printer Objects using active directory service.
- Domain Controller allow user access to any machine connected to AD
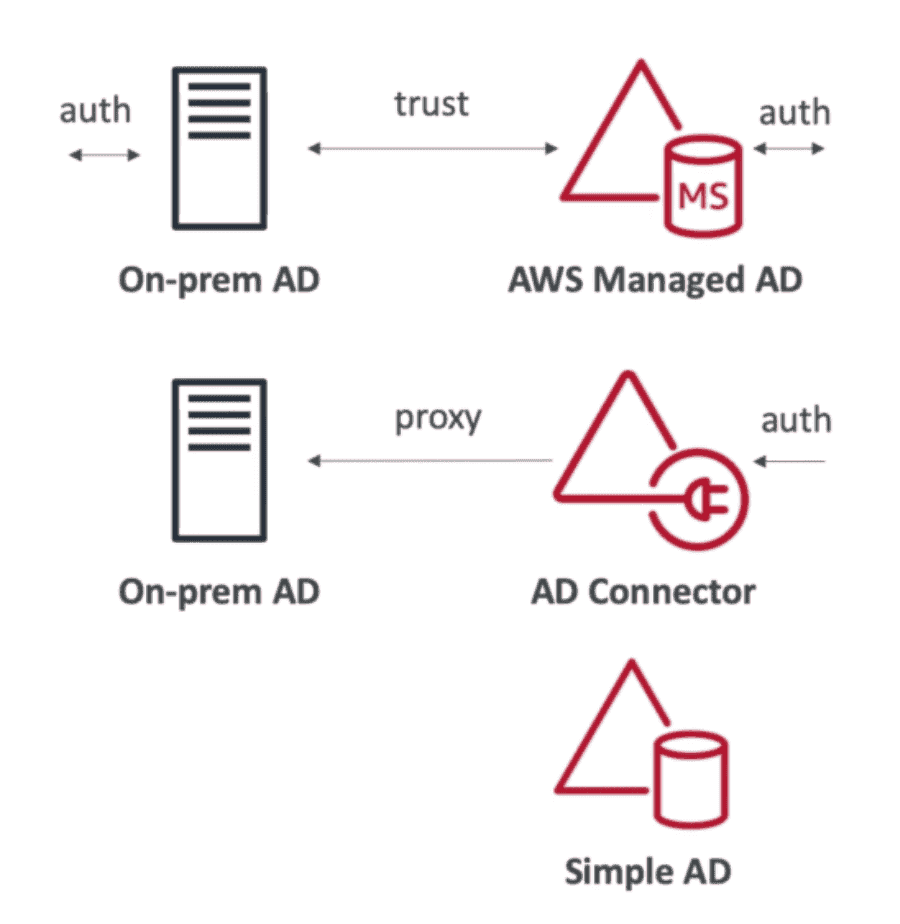
Flavour
- 1. AWS Managed AD:
Create own AD on AWS or connect with on-premise AD using
Trust.- Support MFA
- 2. AD Connector :
Use
Proxyto route on-premise AD to AWS. User manged in on-premise AD.- connect from 500-5000 users
- 3. Simple AD
StandaloneAD on AWS. Cant use with on-premise AD- Cant be used with on premise AD
SSO Single Sign On AUTHENTICATION
- Single Login to access all accounts on Organization
- Support SAML 2.0 Markup
- Can be integrated with on premise AD, AWS Console, Business Cloud Apps as well as Custom SAML
ENCRYPTION
AWS KMS (KEY MANAGEMENT SYSTEM)
Create keys to Encrypt data in Transit & Rest
- AWS Mange Encryption Keys: Fully integrated with IAM
<=4KB: use Encrypt/Decrypt API>4kB: Useenvelop encryptionusing Generate Data Key- Key Rotation happen every
1 year - Supported by SDK ( Java, Python, C, JavaScript) & CLI
- Key is Bound to a Region: While copying Snapshots we need to re-encrypt using new KMS Key
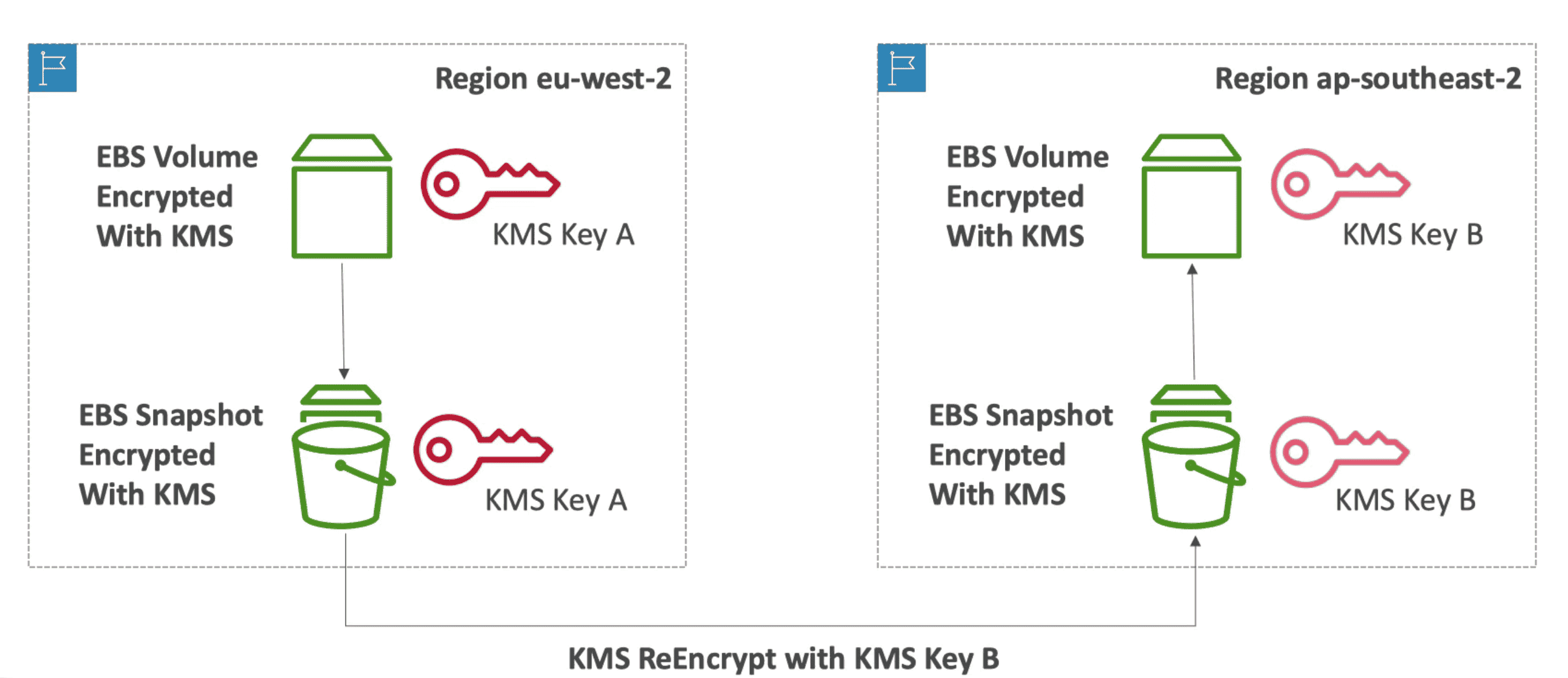
Encryption of data on Storage & DB
- Encryption enabled by default:
EFS - Support Encryption:
- EBS, S3
- RDS, Redshift, ElastiCache,
- AWS Lambda, Amazon SageMaker.
DataKey Caching
Cache Key to reduce number of call to KMS
- Reuse Data key can cause security risk
- LocalCryptoMaterialsCache: Define number of time can be used before key rotation
Throttling Exception
When Quota for KMS Service limit exceed
- KMS share quota for all KMS Key request for a account
- Ways to avoid Throttling
- Exponential Backoff
- Request Quota Increase
- Cache Key using LocalCryptoMaterialsCache
KMS Types
1. Symmetric KMS (AES 256)
Single key for Encrypt/Decrypt
- KMS Key is not available to user
API:
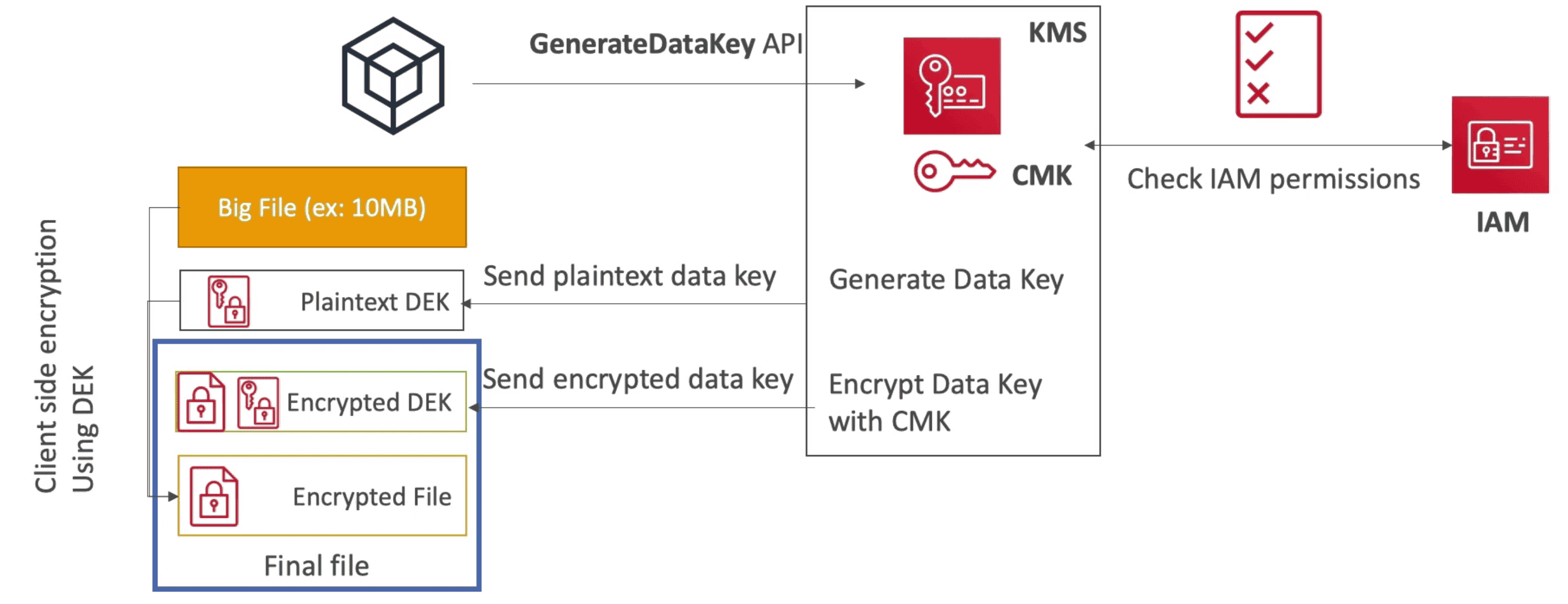
Encrypt,Decrypt: for data upto4kbGenerateDataKey: for data>4kb for Envelope EncryptiongenerateData Encryption Key(DEK)- return plaintext DEK with copy of encrypted DEK under CMK
GenerateDataKeyWithoutPlaintext- create encrypted DEK at some point later which need to be decrypted before use.
GenerateRandom: Random Byte String
Envelop CSE of bigger file using Generated Data Key
Encryption
 Decryption
Decryption
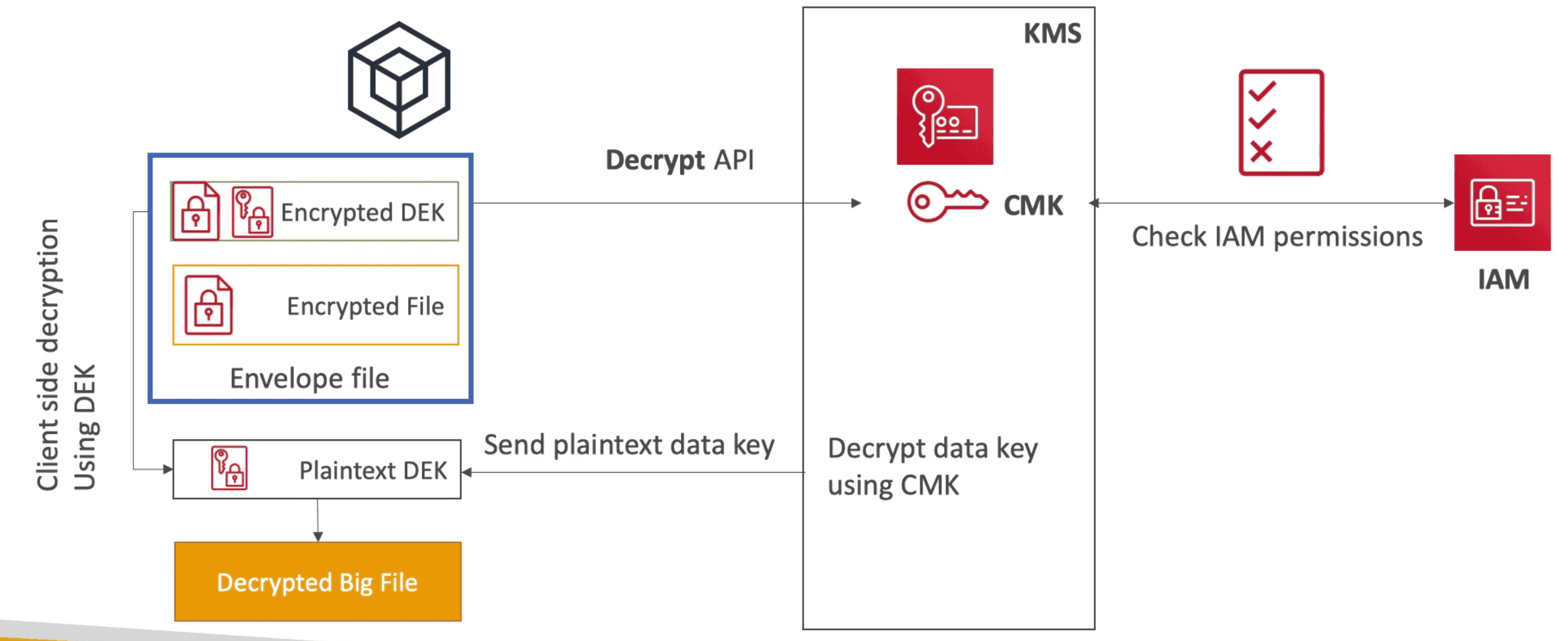
2. Asymmetric KMS (RSA, ECC Key Pair)
Public key(Encrypt) , Private Key(Decrypt) Key pair
- Only Public KMS key is available to user
API:
SignVerify
CMK (CUSTOMER MASTER KEY)
-
AWS Manged CMK(Default)
Create Managed & Used by AWS on behalf of Customer
- Used only by AWS services
- Key Name start with aws/
-
Customer Managed CMK
Create Managed & used by customer
- Cost Money($1/Month)
- Possible to rotate keys
-
AWS Owned CMK
CMK managed & used by AWS services
- AWS use to project account but customer cant see them
-
Cloud HSM Key
Key generated by cloud HSM Hardware
- Operation performed in Cloud HSM cluster
- Expensive
Cloud HSM (HARDWARE SECURITY KEY)
AWS Provisioned encryption hardware
- We Manage the Keys, AWS manage Hardware
- Dedicated Hardware with temper resistance
- Connect with CloudHSM Client to manage keys
KMS Policy
Policy to Control access to your KMS CMKs
- Without Policy no one can access keys: Policy allow user to access Keys.
- IAM Policy should allow calling KMS to access Key
- Default Policy: Allow Root user access to KMS
- Custom Policy: Define user & role who can access & manage key
Server Side Encryption (SSE-KMS)
User controlled KMS Key used for SSE
- Set
"x-amz-server-side-encryption":"aws:kms"as header inHTTP/Scall for upload object - User Controlled KMS allow Audit trail
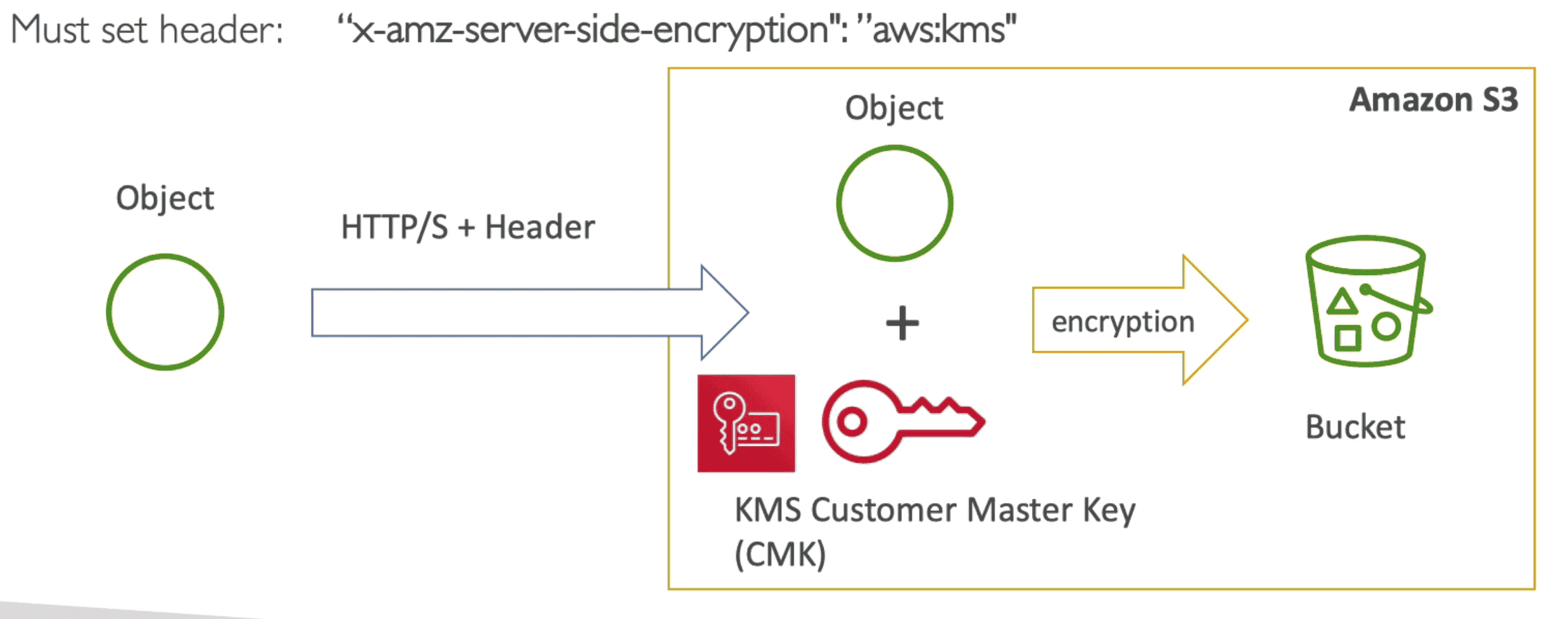
- Make use of
GenerateDataKey&DecryptAPI - KMS Key logs show in CLoudtrail logs & Quota get decrease KMS Quota Limit
Security Enhancement Agents
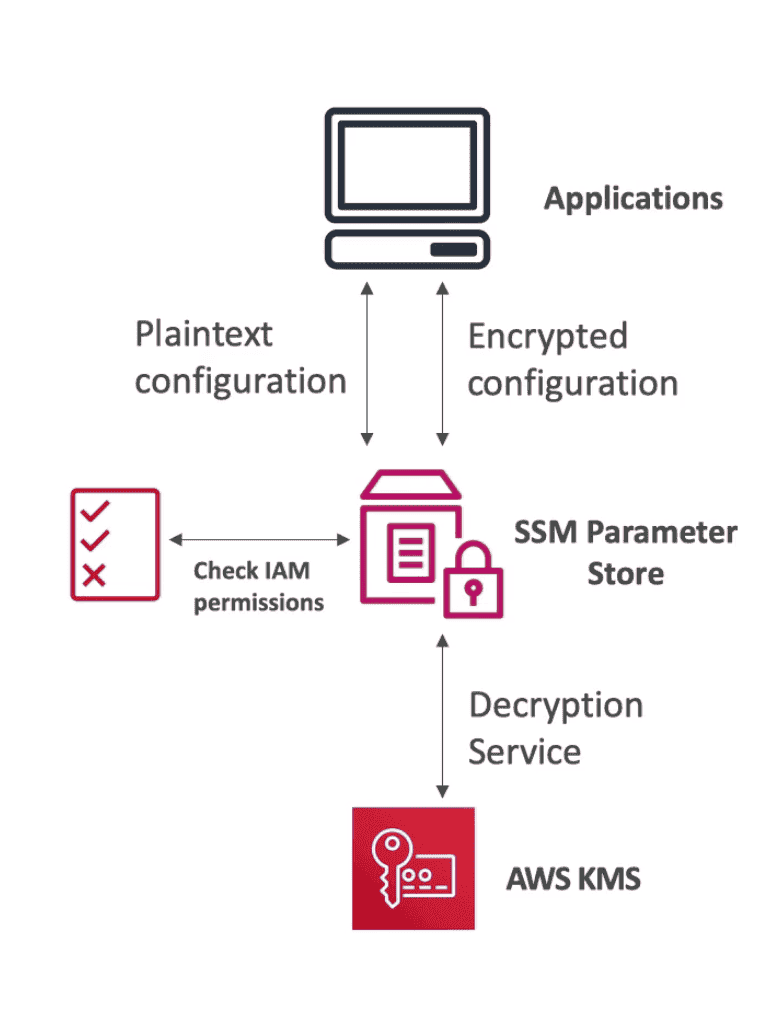
SSM Parameter Store
store secrets & Config with help of Systems Manager(SSM)
- Allow versioning of secret & config
- serverless, scalable, easy to use sdk
- Seamless Encryption using KMS
- Integration with CLoudFormation & CloudWatch
| Feature | Standard | Advanced |
|---|---|---|
| Parameter/AWS Account | 10k | 100k |
| Max Parameter Size | 4kB | 8kB |
| Parameter Policy | NO | YES |
| Storage Cost | Free | $.05 /parameter/month |
| Standard Throughput | Free | $.05/10k API |
| Higher Throughput | $.05/10k API | $.05/10k API |
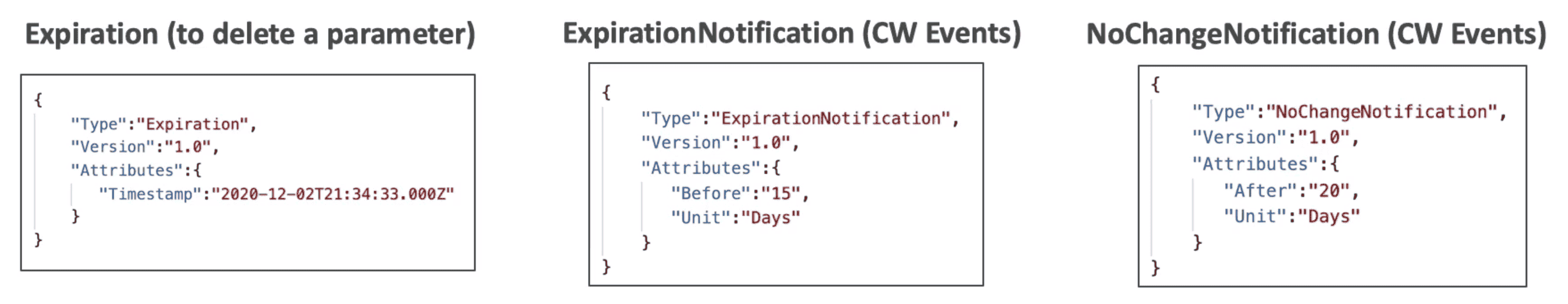
Parameter Policy
Allow to assign TTL to force update Parameter Store
- Only supported by Advanced ssm parameter store
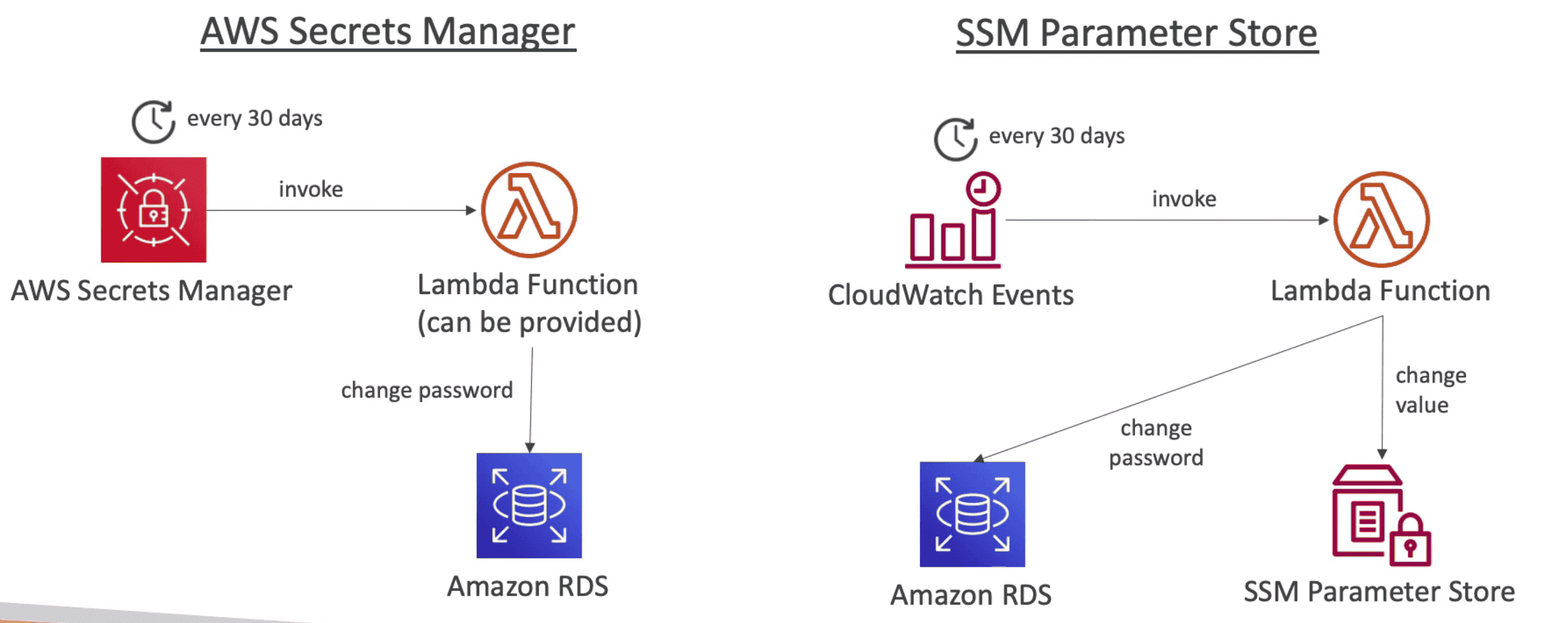
AWS Secret Manager
paid service to Store Secret after SSM Parameter store
- Option to force
Rotation of secret every X day - Automate Secret Generation using
AWS Lamda - Integrated with
RDS DynamoDB, RedShift,DBto create password for DB - Encrypted with KMS
- Price: $.4/secret/Month
- Throughput: $.05/10k API
| Feature | SSM Parameter Store | Secret Manger |
|---|---|---|
| Cost | More Expensive | Less Expensive |
| Rotation | Automatic using Lambda | No Auto Secret Rotation |
| Usage | Integrated with DB | |
| Encryption | KMS Mandatory | Optional |
| Cloudformation Integration | Supported | Supported |
ACM (AWS CERTIFICATE MANAGER)
Allow to provision & maintain SSL/TLS Certificate
- Provide
HTTPSend points - Support public & private TLS Certificate
- Free of charge for TLS
- Support Automatic renew of TLS
- Load onto
- Elastic Load Balancer
- API gateway
- CloudFront to offer HTTPS to client traffic
SNI (Server Name Indication)
List of certificate to supported by list of host name to create SSL connection to ELB
- Load multiple Certificate to one web server
- Works with
ALB,NLBto support multiple Certificate for Multiple Listeners - Supports Cloudfront
- Does not support CLB
AWS Artifact
Give Compliance report for internal Audit or Compliance
-
AWS Artifact Reports: compliance reports of AWS audited by from third-party auditors.
-
AWS Artifact Agreements: Service provide access to agreement HIPAA, BAA or for organization
ML Analysis Tools
AWS Inspector
Automatic Security assessment to find Security Vulnerability in
EC2 instance
- Agent install & run Only on EC2 Instance
- Can be run once, weekly
- Agent can be installed in all EC2 instance for account
- Create list of Assessment Findings
- Analyse OS against Security vulnerability
- Analyse against unintended network accessibility
- Security Best practices
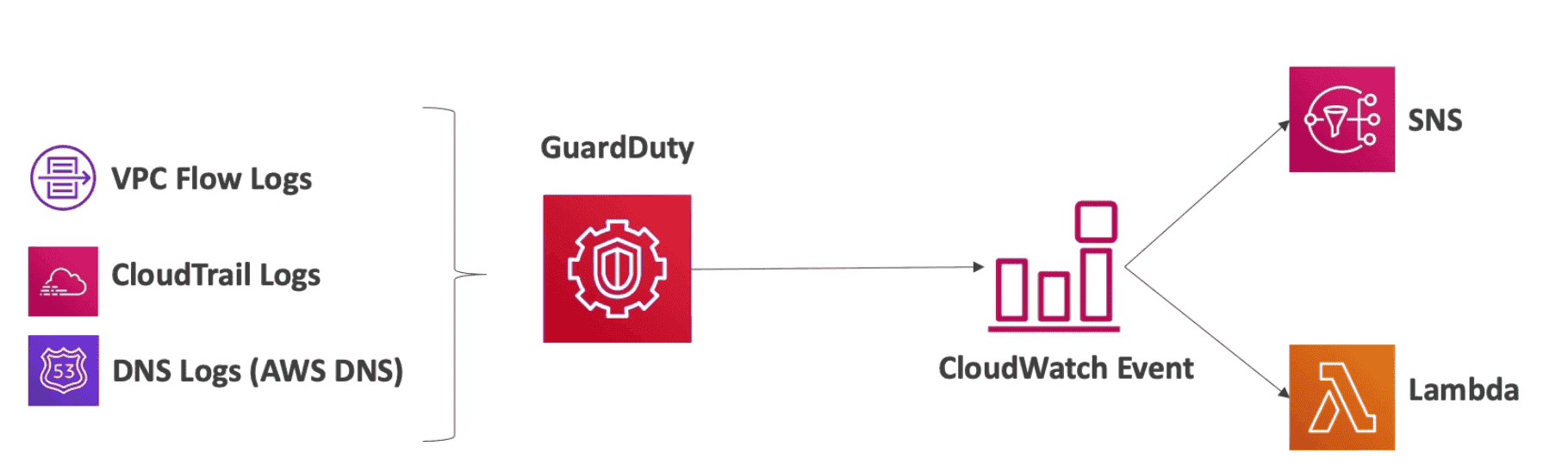
Guard Duty
Intelligent Threat Discovery by Analysis Logs
- Detect anomaly and unauthorize API calls from various sources using ML
- No installation required with 30 days trial
- Can trigger Lamda function or SNS topic with help of Cloud Watch
- Protect against
Crypto Currency Attack
Continuously Analysis Logs from:
- Cloud trail logs
- VPC Flow Logs
- DNS Logs
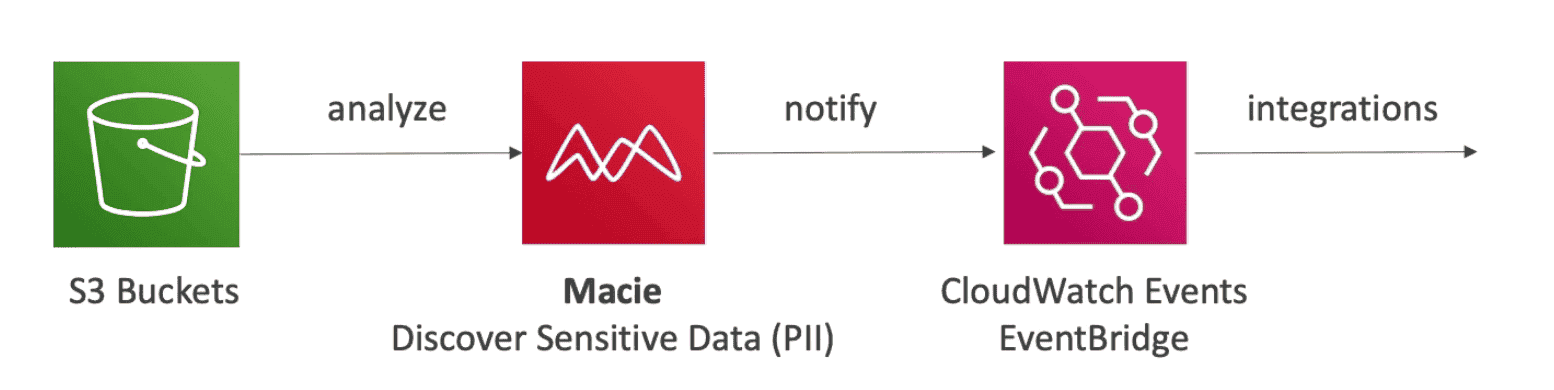
Macie
Fully managed data security & data privacy service
- Discover & protect sensitive data in
AWS S3using ML & pattern matching. - Use Cloud watch to inform
PII(Personal Identifiable Information) - Create Alert around sensitive Data stored in DB/Storage to trigger SNS or Lambda
Amazon Detective
Analyze Investigate the root cause of security issue or suspicious Activity
- Help speed up finding security hole with help of ML
- Automatically collect logs form VPC flow, Cloud Trail, Guard Duty & create unified view
AWS Compute Optimizer
Provides a set of APIs and a console experience to help you reduce costs and increase workload performance by recommending the optimal AWS resources for your AWS workloads.
- Reduce costs by using ML to analyze your resources' configurations and their utilization.
- Optimize: EC2, AutoScaling Group, EBS, Lambda
AWS Trusted Advisor
Web service that inspects AWS environment and provides real-time recommendations in accordance with AWS best practices
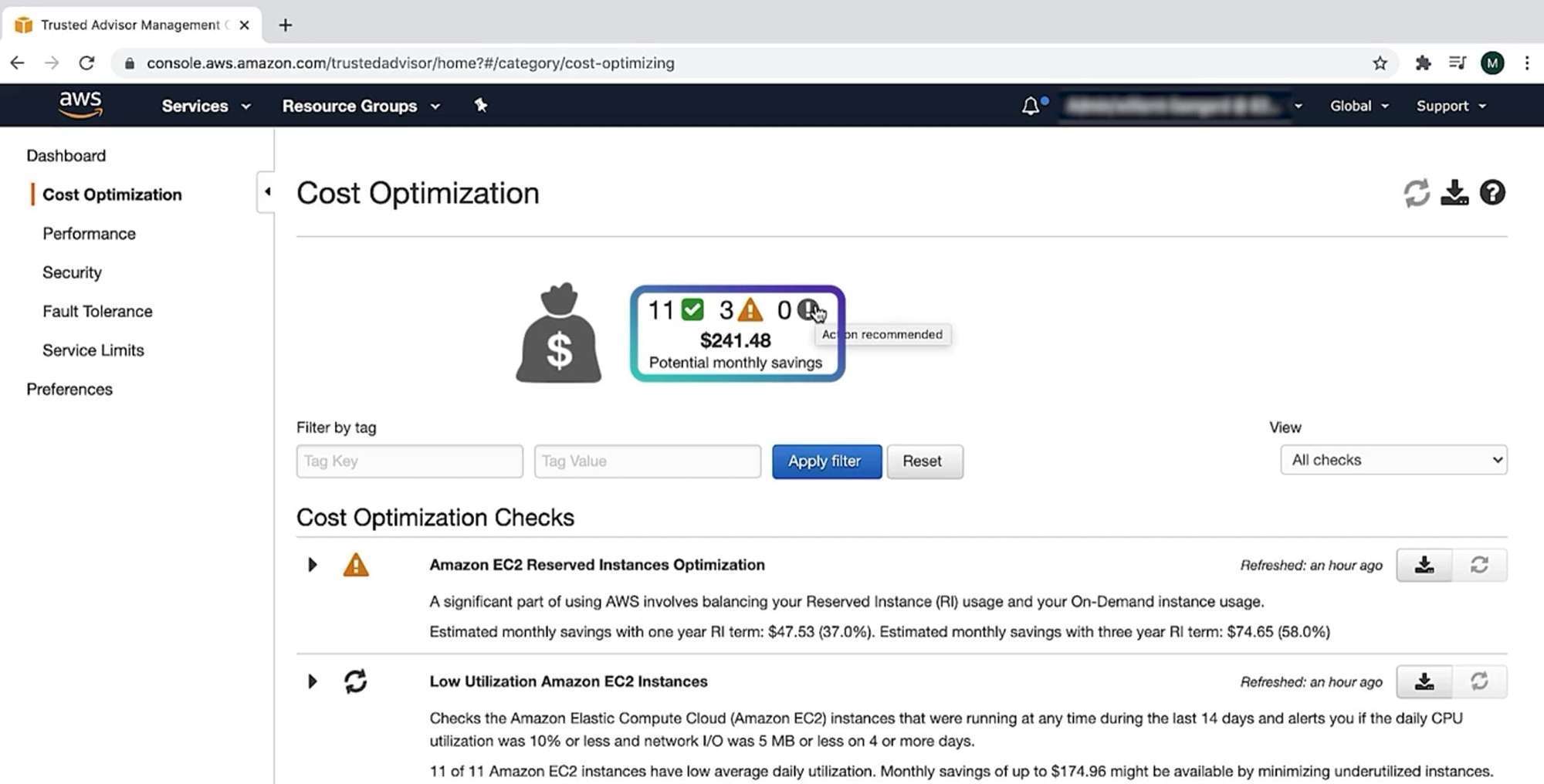
Evaluate Resources against: *(Important for Exam)
- Cost Optimization
- identify unattached or underutilized EBS volumes
- low used EC2 Instance & Idle Load Balancer
- Reserved instance & saving plan optimization
- Performance
- Over utilize EC2 Instance
- EC2 to EBS Optimization
- Cloudfront, CDN Optimization
- Security: 7 Core Check *(Important for Exam )
- S3 Bucket Permission: Bucket is not public
- Security Group: specific port not unrestricted eg SSH
- MFA on root account
- IAM Use: at least 1 IAM user
- MFA on root account: Multi factor authentication on root account
- EBS public snapshot:
- RDS Public snapshot:
- Service Limit in AWS:
- Fault Tolerance
- EBS Snapshot age
- Multi AVZ Configuration: RDS, ELB
- Service Limit
- Reaching service Quota
Full Check
- Available only with
Business & Enterprise Plans - Cloudwatch alarm when reach service limit
- Programmatically access AWS Support API
Alert Levels
- ✅: no problems.
- ⚠️: recommended investigations.
- 🔴: recommended actions.
Infrastructure Security
DDOS (Distributed Denial of Service)
flood a website or application with excessive network traffic until the targeted website or application becomes overloaded and is no longer able to respond.
1. AWS Shield Standard
- Free: Protects all AWS customers at no cost
- Protect on Layer 3/4
- Protect from most common, frequently occurring types of DDoS attacks.
- Real time automatic mitigation
2. AWS Shield Advanced
Detect and mitigate sophisticated DDoS attacks
- Paid Service: $3000/month/organization
- 24/7 Response Team
- Protection from higher resource usage during DDoS attack
3. Web Application Firewall (WAF)
Protect from Web exploits
SQL Injection & Cross SiteScripting XSS
- Operate on Layer 7 HTTP Layer of OCI Model
- Work on:
Application Load balancer, API gateway, Cloud Front - Define Web ACL (Access Control List)
- geo-match: Blacklist Country
- IP Address, Header, Body
- SQL Injection & Cross Site XSS
- Rate based rule(Max request per user)
NETWORK ACCESS CONTROL LIST (Network ACL)
- Stateless
- Subnet Level Security on VPCS
- Block request entering or exiting subnet
- By default allows all traffic in & out
- Custom ACL deny all traffic until specified which traffic to allow
SECURITY GROUP
- Stateful
- EC2 Instance level Security operate at Network Level
- Outbound traffic allowed by default inbound traffic allowed after check.
- All EC2 Instance are assign to security group
- By Default Security Group block all requests
- Security rules must modify to allow specific type of traffic eg HTTPS
AWS Firewall Manager
a security management service that allows you to centrally configure and manage firewall rules across your accounts and applications in AWS Organizations.
- integrated with AWS Organizations to enable
- AWS WAF rules,
- AWS Shield Advanced protection,
- security groups,
- AWS Network Firewall rules,
- Amazon Route 53 Resolver DNS Firewall rules.
Penetration Testing
Allowed to test 8 services without prior approval
- EC2
- RDS, Aurora
- Cloudfront
- Lamda & Edge Function, API Gateway
- Lightsail
- Elastic Bean stalk
