SECURITY
Azure Security Center
Monitoring service that provides visibility of security posture across all services, both on Azure and on-premises.
Security Layers (available to use in cloud computing):
- Data: Vnet endpoint, limit SQL Server user rights
- Application: run API management in front of APIs
- Compute: limit remote desktop access, limit SSH, run timely update
- Network: NSG, use subnets, deny traffic by default
- Perimeter: DDoS protection, firewalls, WAF
- Identity & access: Azure AD
- Physical: Door locks, fingerprint readers, and key cards
Azure Organization
The Azure account
An identity in
Azure ADor in a directory that Azure AD trusts.
- A global unique entity that gets you access to
Azure services & Azure Subscriptions.
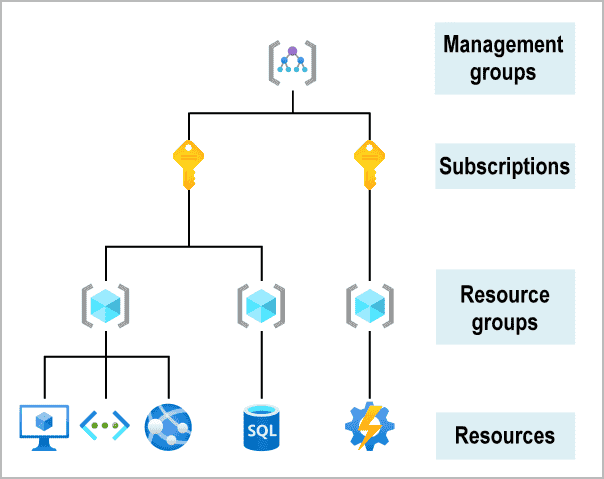
Azure MANAGEMENT GROUP
Help manage access, policy, and compliance for multiple subscriptions.
- All subscriptions in a management group automatically inherit the conditions applied to the management group.
One To Many(1:N): management group can have many children.
One to One(1:1) Can support only one parent.
Limitations
10kManagement groups/ AD.- Support up to
6levels of depth. This limit doesn't include the root level or the subscription level. - All subscriptions and management groups are within a single hierarchy in each directory.
Usage:
- Manage governance across multiple Azure
subscriptions
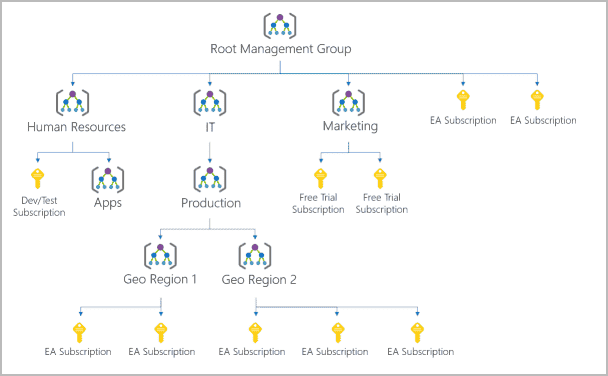
Azure SUBSCRIPTION
Logical unit of Azure services that links to an Azure account.
- Object that represents a container that you can put resources in.
- Authentication and Authorized : Allow/Deny access to Azure products and services using trust relationship with an Azure Active Directory (Azure AD) instance.
One To Many(1:N): Can create multiple Subscriptions in your Azure account to create separation for billing or management purposes.
One to One(1:1): Can support only one parent.
Usage
- Manage resources in resources groups.
- Grouping: Groups together user accounts & the resources that have been created by those user accounts.
- Provision resources: Set Quotas on the amount of resources that can be created and use.
- Billing and Budget: Manage costs and the resources that are created by users, teams, or projects.
Azure BLUEPRINT 
Templates for subscriptions, so that new subscriptions already come with a default set of users and policies.
- Help to quickly build and deploy new environments that are always compliant with organizational standards
Blueprint LifeCycle
- Creation of a blueprint
- Publishing of the blueprint
- Creating or editing a new version of the blueprint
- Publishing a new version of the blueprint
- Deletion of a specific version of the blueprint
- Deleting the blueprint altogether
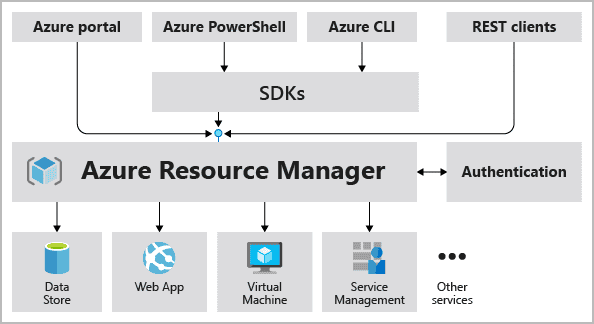
Azure RESOURCE MANAGER(ARM)
Deployment and management service to provide a management layer that allows to create, update, and delete resources.
- Deploy, manage, and monitor all the resources for your solution as a group.
- Access control with help of RBAC.
- Use tags to logically organize resources.
- Viewing costs for a resources group sharing same tag.
Resource Manager template
JSONfile that defines what you want to deploy to Azure.
-
Infrastructure as Code: Manages infrastructure through Declarative templates rather than scripts.
-
Redeploy solution in a consistent state each time.
-
Deploy dependent resources in the correct order
"resources": [ { "type": "Microsoft.Storage/storageAccounts", "apiVersion": "2019-04-01", "name": "mystorageaccount", "location": "westus", "sku": { "name": "Standard_LRS" }, "kind": "StorageV2", "properties": {} } ]
The template has the following sections:
Resources - Specify the resources to deploy.
Parameters - Provide values during deployment that allow the same template to be used with different environments.
Variables - Define values that are reused in your templates. They can be constructed from parameter values.
User-defined functions - Create customized functions that simplify your template.
Outputs - Return values from the deployed resources.
Template can be deployed using:
- Azure portal & Cloud Shell
- Azure CLI & PowerShell
- REST API
- Button in GitHub repository
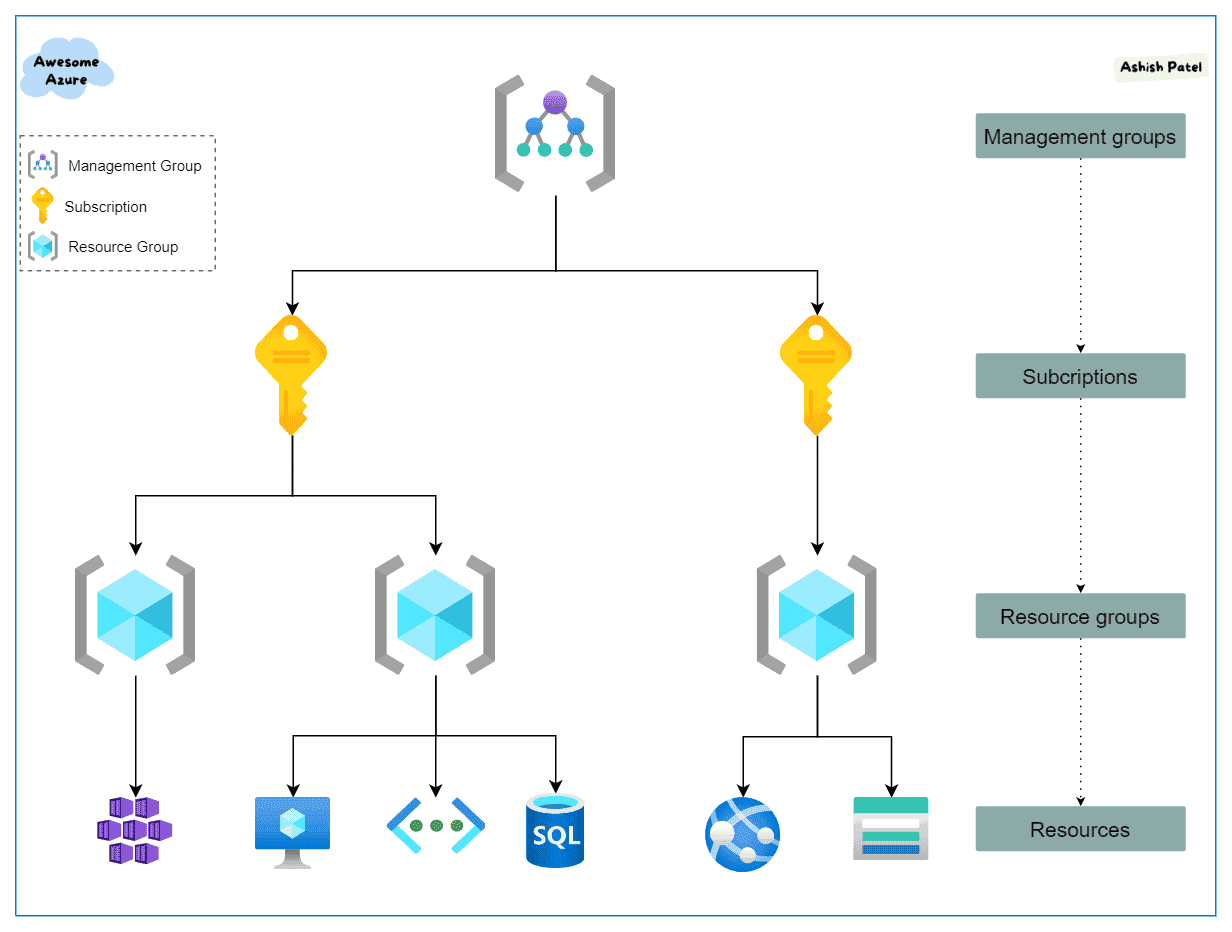
RESOURCE GROUPS 
Logical container into which combine resource groups for access control & management.
- If a resource group is deleted, all resources contained within it are also deleted.
- Scope of
role-based access control (RBAC)for applying permissions on set of resource.

RESOURCES
Resources are instances of services that you create, like virtual machines, storage, or SQL databases.
Resource Access Management
Role-Based Access Control (RBAC)
assigning permissions by role instead of to individuals one by one
Locks
it allows you to “lock” resources to prevent them from being changed without removing the lock
- an easy way to stop someone from accidentally stopping or deleting an important resource
Locks Access Control
you can limit who has the ability to delete locks
Network Security Group (NSG)
a fairly basic set of rules that you can apply to both inbound traffic and outbound traffic that lets you specify what sources, destinations and ports are
- allowed to travel through from outside the virtual network to inside the virtual network
 Application Security Group (ASG)
Application Security Group (ASG)
A way of grouping related resources together to simplify the way NSG rules are created.
- ASGs are used within a NSG to apply a network security rule to a specific workload or group of VMs
- All front end VMs can be in one ASG, while the mid-tier is in another.
- Provide granular security traffic controls to improve isolation of workloads and can protect them individually.
KEY/SECRET MANAGEMENT
Azure Key Vault 
securely store and tightly control access to
tokens, passwords, certificates, API keys, and other secrets.
Azure Vaults support: software and HSM-backed Vault
- Secure: Authorization using
RBACor Key Vault access Policy. - Monitor: enabling logging for vault
- Centralizing storage of application secrets
- Secure in Transit: Enforces Transport Layer Security protocol.
Hardware security modules (HSMs)
crypto processor specifically designed to protect cryptographic keys throughout their life cycle.
- These secrets and keys can be protected either by software or by FIPS 140-2 Level 2 validated HSMs.

Usage:
-
Secret Management Securely store and tightly control access to tokens, passwords, certificates, API keys, and other secrets
-
Key Management solution Create and control the encryption keys used to encrypt your data.
-
Certificate Management: provision, manage, and deploy public and private Secure Sockets Layer/Transport Layer Security (SSL/TLS) certificates for use with Azure and your internal connected resources.
Best Practice
-
Manged Identities: use managed identities to VM that access resources.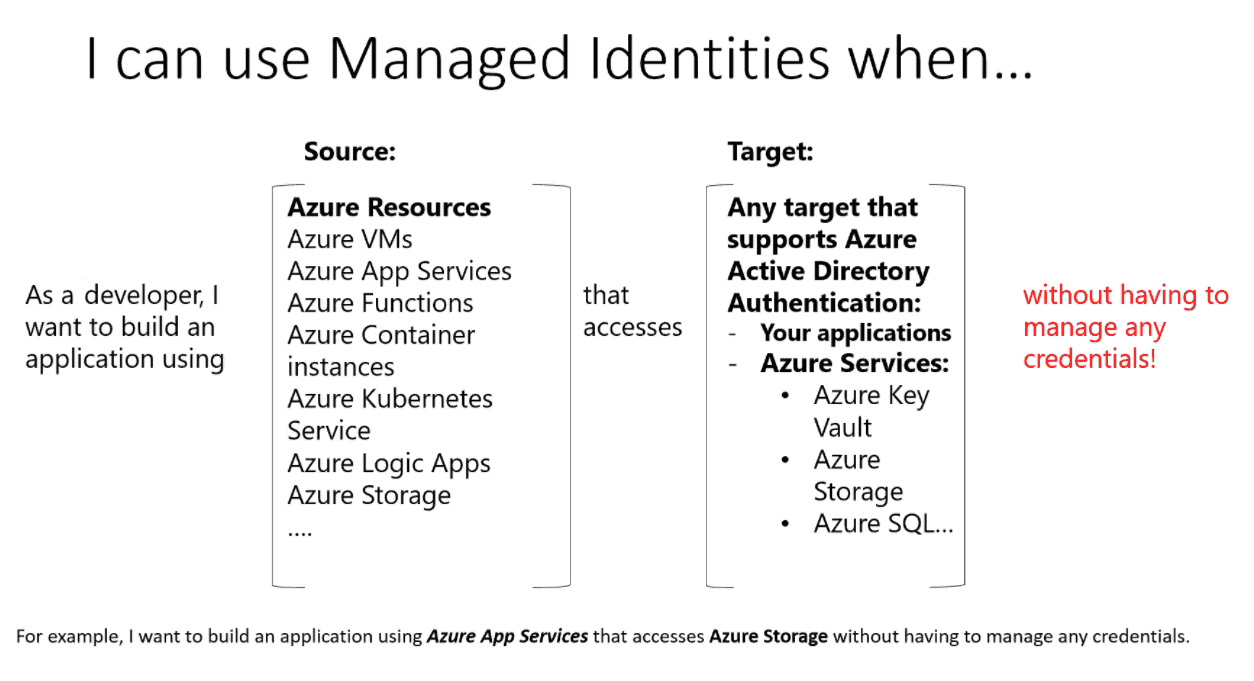
-
Use separate key vaults: 1 vault per application per environment (Development, Pre-Production and Production).
-
Control access to your vault: allow only authorized applications & users.
-
Backup: regular backups of your vault on update/delete/create of objects within a Vault.
-
Logging: Turn on logging and alerts for tracing.
-
Recovery options: Turn on soft-delete and purge protection to guard against force deletion of the secret.
Azure APP CONFIGURATION
Complements Azure Key Vault by making it easier to centrally manage
application settings and feature flags.
Advantages:
- Centralize management : distribution of hierarchical configuration data for different environments and geographies
- Dynamically change application settings without the need to redeploy or restart an application
- Real Time Control feature availability
- Secure: encrypted at rest and in transit by
AES256Azure Manged Encryption Key
Feature:
- Fully managed service that can be set up in minutes
- Flexible key representations and mappings Tagging with labels
- Point-in-time replay of settings
- Dedicated UI for feature flag management
- Comparison of two sets of configurations on custom-defined dimensions
- Enhanced security through Azure-managed identities
- Complete data encryptions, at rest or in transit Native integration with popular frameworks
KEY
-
Case-sensitive (app1 != App1)
-
unicode-based strings except
*,,, and\but can be escaped -
Combined size limit of
10kchars on key-value pair. -
hierarchy using character delimiter:
/ or :AppName:Service1:ApiEndpoint AppName:Service2:ApiEndpoint AppName:Region1:DbEndpoint AppName:Region2:DbEndpoint -
Label Key: used to create environment. Default: empty, or nullKey = AppName:DbEndpoint & Label = Test Key = AppName:DbEndpoint & Label = Staging Key = AppName:DbEndpoint & Label = Production -
Version: doesn't version key use Label+ Git Hash to create Versions -
Query: using Regex Pattern Matching
Security of App Configuration
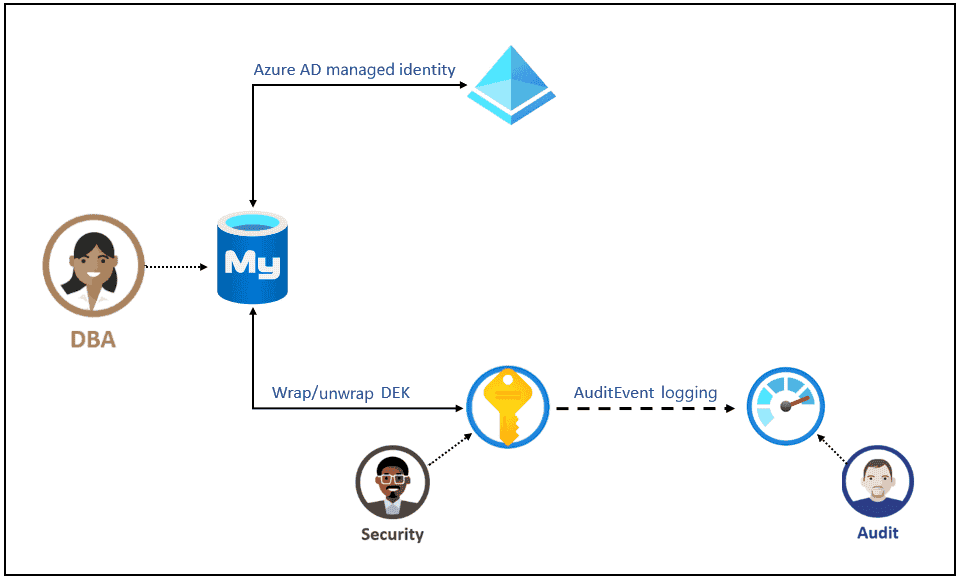
wrapKey: To be able to encrypt the DEK.unwrapKey: To be able to decrypt the DEK.
Customer-managed keys
- App Configuration uses a managed identity assigned to authenticate with AAD to calls Azure Key Vault and wraps the App Configuration instance's encryption key.
- The s encryption key is then stored and the unwrapped encryption key is cached within App Configuration for one hour.
- App Configuration refreshes the unwrapped version of the App Configuration instance's encryption key hourly.
Use Private endpoints
Network interface that uses a private IP address from VNet.
- This network interface connects privately and securely to a service that's powered by Azure Private Link without going over the INternet
Use Managed identities
AAD allows Azure App Configuration to easily access Azure Key Vault
NETWORK SECURITY TOOLS
[**Microsoft Defender for Cloud
**](https://docs.microsoft.com/en-us/azure/defender-for-cloud/defender-for-cloud-introduction)
Cloud Workload Protection Platform (CWPP) that also delivers Cloud Security Posture Management (CSPM) for all Azure, on-premises, and multi-cloud (Amazon AWS and Google GCP) resources.
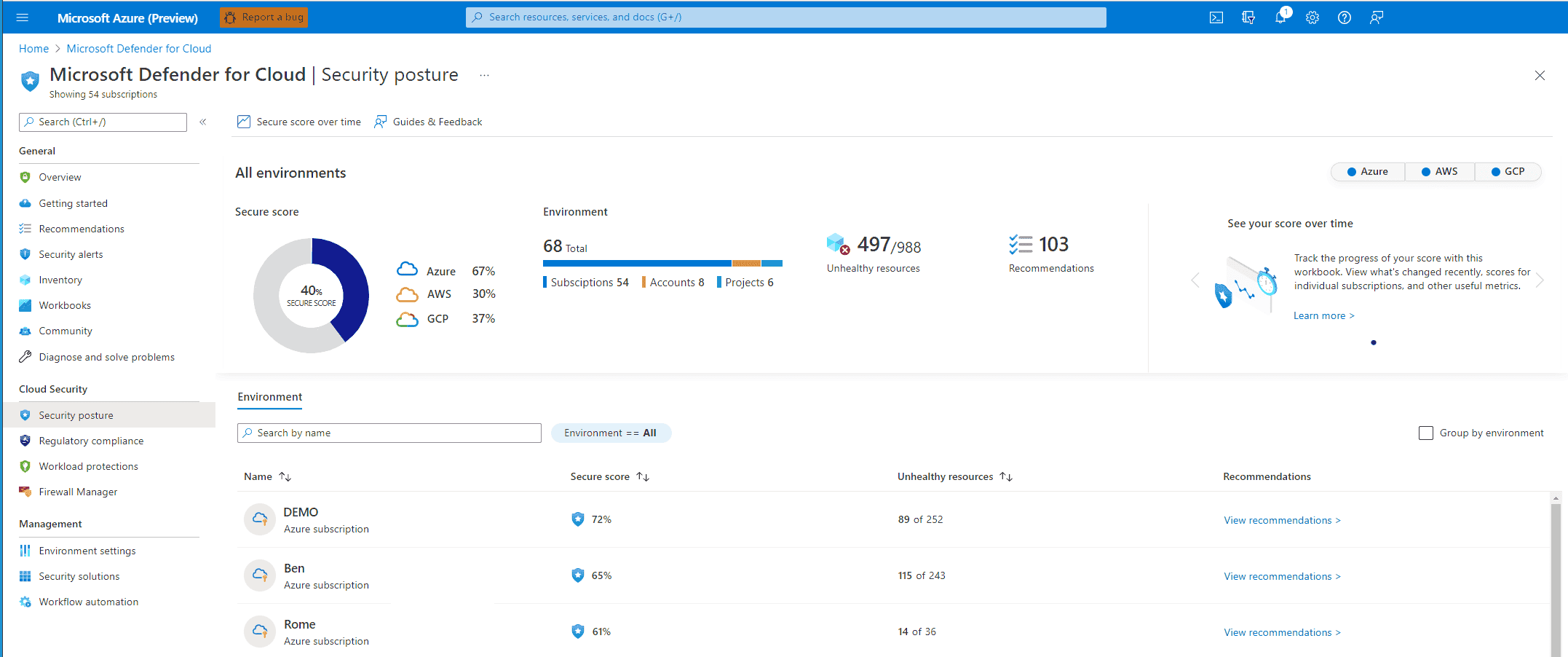
1. Secure-> Recommendations
Remediate potential security vulnerabilities in your Azure resources.
- Identify cloud workloads that require security actions
- provide steps to protect workloads from security risks.
2. Continuous assessment -> Secure score
Gives a clear view of security posture based on the implementation of the security recommendations
- Track new security opportunities and precisely report on the progress of security efforts.
- Higher the score, the lower the identified risk level.
3. Defend -> Alerts
Warn about security events in your workloads in real-time, including the indicators that led to the event.
Just-in-time (JIT): you to lock down inbound traffic to your Azure virtual machines.

Pricing:
- Per hour for VMs, app services, SQL database
- Per transactions for storage and IoT messages
- Per month for IoT devices
- Per image for ACR
- Per vCore/hour for AKS
Microsoft Defender for Identity 
identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization.
- (formerly Azure Advanced Threat Protection, also known as Azure ATP)
- Identify, detect, & investigate advanced threats in organization.
- Allows to monitor user activities and information.
- Identify & investigate advanced threats throughout the entire cyber-attack kill chain:
Reconnaissance
Identify rogue users and attackers' attempts to gain information.
Compromised credentials
any attempts that compromise user credentials shall be detected.
Lateral movements
Detect attempts to move laterally inside the network to gain further control of sensitive users, utilizing methods such as Pass the Ticket, Pass the Hash, Overpass the Hash and more.
Domain dominance
The attacker try to remote code execution on the domain controller, and methods such as DC Shadow, to access domain controller.
Exfiltration
unauthorized data transfer.
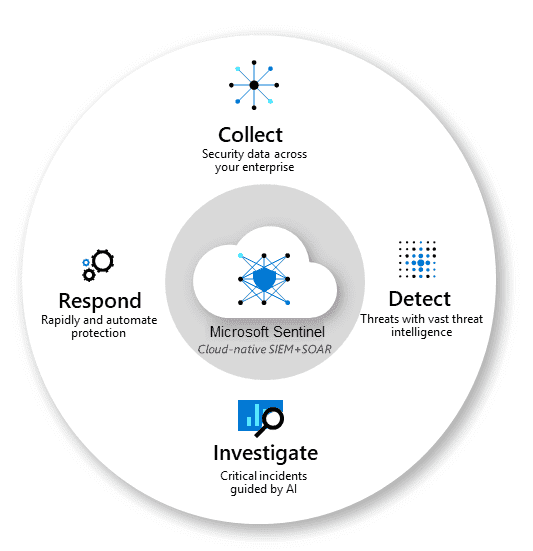
 Microsoft Sentinel
Microsoft Sentinel
Intelligent security analytics and threat intelligence service that provides alert detection, threat visibility, proactive hunting, and threat response.
-
scalable, cloud-native, security information and event management (
SIEM) and security orchestration, automation, and response (SOAR) solution. -
Provide deep investigation tools to find the root cause of a potential security threat.
-
Automate tasks and simplify security orchestration using playbooks.
-
Gain insights across your data with Azure Sentinel Workbooks.
-
Investigate and resolve possible threats with incidents (groups of related alerts).
Core Capabilities
1. Collect
Connect data from all your sources for deeper security intelligence.
2. Detect
use AI to analyze data & detect threats
3. Investigate
Use built-in dashboards and queries to view and analyze your data.
4. Respond
Reduce alert fatigue and false positives so you can focus on what matters.
Pricing
- Data retention is charged after 90 days.
- Charged for the ingested data (per GB).
DDoS protection services
Natively integrated into Azure. Includes configuration through the Azure portal.
1. Basic
mitigates common network attacks.
- Enabled by default (free).
- Both basic and standard protects IPv4 and IPv6 public IP addresses.
2. Standard
advanced capabilities to protect you against network attacks such as logging, alerting, and telemetry.
- Pay for the processed data every month (per GB).
- Logging: Real-time attack metrics and resource logs via Azure Monitor
- Alerting: alerts at the start and stop of an attack.
- Telemetry: Post attack mitigation reports
